Though, it might have done even better in the privacy sub-forum, but we don't have one of those. It wasn't necessarily security - though it could be - related. It depends on how and why you're using it. Kinda like how a hammer is a tool or a weapon, depending on what you're doing with it at the time!
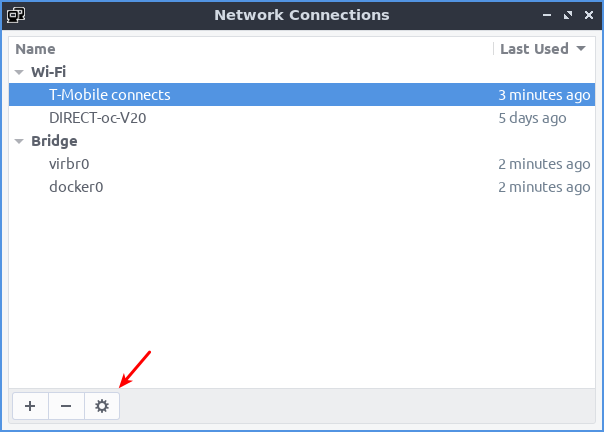
What is it? Changing your DNS servers. If you want to change DNS servers, it's not all that complicated. I even used ChatGPT to write a couple of paragraphs to explain what DNS was, though I usually just sum it up as being similar to a telephone book. ChatGPT did a much better job than I do, so I included it.
 linux-tips.us
linux-tips.us
I do love me some feedback, but I'll be in and out today. On top of that, my connection to the web is a bit touchy today.
What is it? Changing your DNS servers. If you want to change DNS servers, it's not all that complicated. I even used ChatGPT to write a couple of paragraphs to explain what DNS was, though I usually just sum it up as being similar to a telephone book. ChatGPT did a much better job than I do, so I included it.
How To: Change DNS Servers • Linux Tips
Today's article shouldn't be all that difficult for even our newest users, but is limited to those who want to change DNS servers.
I do love me some feedback, but I'll be in and out today. On top of that, my connection to the web is a bit touchy today.