truckerDave
Active Member
GOALS:
I am thinking of something along the lines of this image
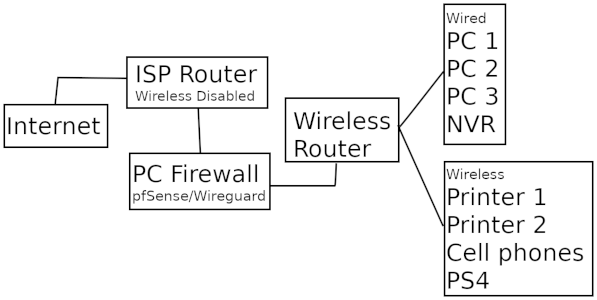
I've read/watched several articles/videos about hardware routers, pfSense and Wireguard. I'm still uncertain about Wireguard as everything I have viewed goes through all the "great reasons to use it" and the whole set up process . But after 3 evenings of looking, I've yet to see anyone actually show how to use the program beyond installation and setup. It goes without saying, I'm no network engineer. And after reviewing the Wireguard website, I'm afraid it may be over my head. I'm the sort where if you show me how to cook something I like, I can make that dish the rest of my life. Hand me a recipe, and I'll screw it up.
I do intend on adding the firewall. However, I may opt for OPNSense. Still undecided.
I've also thought about, after adding the firewall, to set it up to only allow my cell phone's IP to access the server via some obscure port. But not sure how secure that would be. But it would probably be more within my knowledge base.
Thoughts? Pointers? Criticisms? Am I going about this all wrong?
- Ditch Windows (Done)
- Server for my business records (Apache, PHP, MySql)(Done)
- Have access from afar
I am thinking of something along the lines of this image
I've read/watched several articles/videos about hardware routers, pfSense and Wireguard. I'm still uncertain about Wireguard as everything I have viewed goes through all the "great reasons to use it" and the whole set up process . But after 3 evenings of looking, I've yet to see anyone actually show how to use the program beyond installation and setup. It goes without saying, I'm no network engineer. And after reviewing the Wireguard website, I'm afraid it may be over my head. I'm the sort where if you show me how to cook something I like, I can make that dish the rest of my life. Hand me a recipe, and I'll screw it up.
I do intend on adding the firewall. However, I may opt for OPNSense. Still undecided.
I've also thought about, after adding the firewall, to set it up to only allow my cell phone's IP to access the server via some obscure port. But not sure how secure that would be. But it would probably be more within my knowledge base.
Thoughts? Pointers? Criticisms? Am I going about this all wrong?
Last edited:

