@InvaderSumo
For home users such as us, browser security and privacy is the most important of all other types of security on home PC (or laptop) because web browser is one software which we not only use the most but also we constantly use it to connect to multitude of remote computers many of which are potentially harmful.
Excluding safe computing habits (because you've already been covered with that) browser security and privacy consists of 3 parts:
1.) Running up to date and mainstream web browser, one which receives constant updates
2.) Browser configuration which needs to be as much restrictive as possible, relaxing certain settings only if you require them.
3.) Installing and configuring browser extensions that are essential for both security and privacy.
For point 1 that would be Firefox
For point 2 it should be straightforward to configure it restrictively.
Point 3 is however much more difficult and time consuming, so what follows is short introduction into that part.
In order to configure effective defense with browser extensions there are 2 rules you need to follow:
1.) Rule No.1 is to install as few extensions as possible, ideally only 1-3 but not anything more than that.
2.) And rule No.2 is to install only those extensions which exist for long time and are widely known and trusted by community.
Reason for that is that there are many extensions which are unsafe, especially those made by new authors.
Three extensions which I personally use are:
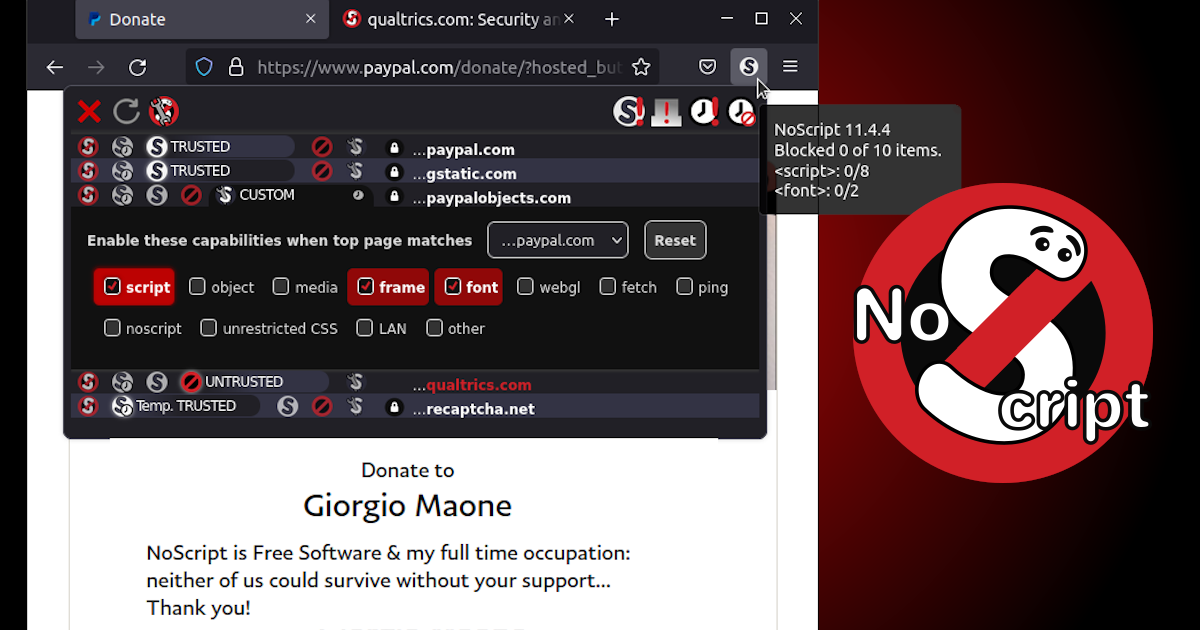
1.) NoScript (To filter domains and selectively block scripts)
2.) uBlock origin (To deal with the ads)
3.) CAD [Cookie Auto Delete] (To auto manage cookies)
Installing these is straightforward and default setup is solid, but in order to configure them for maximum efficiency you first need to familiarize yourself with several terms as follows:
Personal data classification:
1.) Zero party data
- Zero party data is data which you yourself with your own will enter into online forms or into an online account.
2.) 1st party data
- 1st party data is data which the website which you directly visit collects from you trough cookies and similar technologies.
3.) 2nd party data
- 2nd party data is data which a website that you visit acquires about you by purchasing personal information about you from other websites which you visited so far.
4.) 3rd party data
3rd party data is data which a website that you visit learns about you by using 3rd party services that collect information from you, usually those services are trackers and similar.
Knowing the difference is important because each one is attack on privacy requiring separate kind of defense, for ex. defense for one category works best for that category but not equally the same for others.
---
When you visit a website you don't only visit that website, but you usually behind the scene connect to a ton of other domains, defense against which is to effectively configure
NoScript extension.
But to be able to do that here is what you need to know about various domains that you connect to without even knowing it happens all the time and what they do + some examples.
Domain classification:
1.) Static content domains (SCD)
2.) Content delivery network domains (CDN)
3.) Third party cookie domains
4.) Advertising domains
5.) Analytical domains
6.) Tag management domains
7.) Captcha domains
8.) Cookie consent domains
I'll briefly explain each one
1.
Static content domains (SCD) are those which deliver static website content such as images, fonts, media etc.
As such these must not be blocked by an extension.
Example: sstatic.net is used by
stackexchange.com sites to deliver static content
2.
Content delivery network domains (CDN) domains are similar to
SCD except they're world wide improving web page load.
For same reason as with
SCD these must not be blocked.
Example: licdn.com is
CDN domain used by MS's
linkedin.com website
3.
Third party cookie domains are 3rd party domains whose only purpose is to set cookies that are then shared with various parties used to learn user behaviors and habits.
From user's perspective these should be blocked.
Example: ajax.googleapis.com is used by various websites to set 3rd party cookie.
4.
Advertising domains are 3rd party domains whose only purpose is to deliver ads
From user's perspective these should be blocked.
Example: ads-twitter.com is used for twitter ads.
5.
Analytical domains are 3rd party domains which help 1st party in
SEO, they're used to analyze 1st party web traffic to improve performance, provide insights and similar.
From user's perspective these may or may not be blocked.
Example: google-analytics.com is used by various websites for analytical purposes
6.
Tag management domains A tag management system helps manage the lifecycle of digital marketing tags (sometimes referred to as tracking pixels or web beacons), used to track activity on digital properties
Example:
googletagmanager.com
7.
Captcha domains are 3rd party domains which present captcha on 1st party site to confirm visitors are not bots.
These domains should not be blocked.
Example: hcaptcha.com is used by some sites to present captcha
8.
Cookie consent domains are 3rd party domains which present cookie consent to the visitor of the 1st party web site.
These domains should not be blocked.
Example: cookielaw.org is used by some sites to show cookie consent
Now with that knowledge you're ready to configure
NoScript so that those hostile domains cannot invade your privacy.
NoScript also helps to prevent
XSS attacks in addition to other functions.
---
Regarding
CAD extension, you should configure it so that only those cookies about which you care are kept (ex. forum logins) and everything else must be auto deleted as soon as you close a tab or the browser itself.
And regarding
uBlock origin leave it at default and enable only
AdGuard and
uBlock static filters, don't do dynamic filtering because that's done by
NoScript and will lead to duplicate work and slower page load.
Make sure to read documentation to understand how these 3 must have extensions work:
The NoScript Security Suite is Free Software protecting Firefox (on Android, too!), Chrome, Edge, Brave and other web browsers. Install NoScript now!

noscript.net
uBlock Origin - An efficient blocker for Chromium and Firefox. Fast and lean. - gorhill/uBlock

github.com
Firefox and Chrome WebExtension that deletes cookies and other browsing site data as soon as the tab closes, domain changes, browser restarts, or a combination of those events. - Cookie-AutoDelete/...

github.com
If you need help or don't understand something feel free to ask