Just install Red Star OS as your distribution, that way you know for sure you will have someone watching you 

 en.wikipedia.org
en.wikipedia.org


Yes, suspicion is the only reason because there are no sure indicators to prove otherwise.I wouldn't say that, necessarily.
In your OP, at the end, you said
There are software firewall IP tables you can tweak, penetration testing tools you can install, and so on, to have a safer feeling that your security is not being compromised, and so on.
It just depends if you wish to use them or explore them, rather than reinstall.
Uh no way, had enough of big brother.Just install Red Star OS as your distribution, that way you know for sure you will have someone watching you
Rockylinux is a good os but. Redheat currently fight against his clones so i think its better to search for alternatives.I switched from CentOS to Rocly Linux on my vpses, I'm sure Rocky Linux would work as a desktop os as well if CentOS was working before for your family and friends.
I still believe it will be fine with Rocky, another option would be AlmaLinux since they don't claim to be a clone anymore but just ABI compatible.Rockylinux is a good os but. Redheat currently fight against his clones so i think its better to search for alternatives.

* Binary/ABI compatibility in our case means working to ensure that applications built to run on RHEL (or RHEL clones) can run without issue on AlmaLinux. Adjusting to this expectation removes our need to ensure that everything we release is an exact copy of the source code that you would get with RHEL. This includes kernel compatibility and application compatibility.
On other boxes I had no issue with that release-upgrade, alas those were systems that had few changes and a failed or unclean upgrade didn't really worry me.
Just install Red Star OS as your distribution, that way you know for sure you will have someone watching you

Red Star OS - Wikipedia
en.wikipedia.org
dmseg | grep -i swapSo, in some cases... I reinstall the system(s) every day! It's easy!I think I'll erase it all and start again... with Windows.
I guess that needs to be run from each distro, and I haven't done that. The daily driver, Mint Cinnamon, reports a swapfile (but I knew that already). As shown above, I've not yet created a swap partition. If this doesn't all crash and burn quickly, I'll probably add one at the end and make it available to those that need it. Debian only initially wanted 1 GB of swap which I expanded to 4 GB with yesterday's testing. I have 32 GB of RAM.Stan, if you still have those Linux onboard, or else next time you do this, it may be worth running
and see how many of those install with their own Swap catered to.Code:dmesg | grep -i swap
Regarding security and VM. Qubes is the only VM hypervisor (type I) that is really secure so anything else and particularly hypervisors type II are not secure. As mentioned above one need very deep knowledge to test if OS is compromised or not. Not to mention that removal of some RATs may be more expensive hardware replacement.tat -c %w /
2021-07-12 05:17:16.000000000 -0700
Regarding security and VM. Qubes is the only VM hypervisor (type I) that is really secure so anything else and particularly hypervisors type II are not secure.
Well, it was. Wikipedia reports that it's now discontinued (since 2021).If you’re interested in secure Linux distributions, LPS is a notable example.
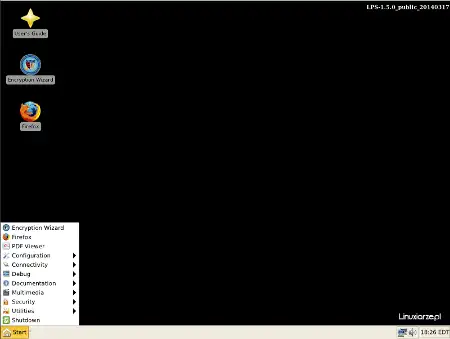
I am talking about VM. Not OS running in RAM. To secure VM you need hypervisor type I and currently the best is Qubes. Qubes lets you running different insecure OSes in a way that VMclient has access to any hardware in a controlled way. So you can install Windows, infect it and observe how malware behaves. After experimenting you can safely delete infected windows without worry that other VM clients get compromised.The United States Department of Defense recognizes the key benefits associated with open-source development and trusts Linux as its operating system. In fact, the U.S. Army is the single largest installed base for Red Hat Linux, and the U.S. Navy nuclear submarine fleet runs on Linux, including their sonar systems1. Additionally, the Air Force has developed a secure Linux distribution called Lightweight Portable Security (LPS), which is designed for secure use. Let me tell you more about LPS:


So, both the U.S. military and other countries recognize the value of Linux for security and operational purposes. If you’re interested in secure Linux distributions, LPS is a notable example.
- Lightweight Portable Security (LPS):
- LPS is a small Linux desktop distribution created by the Software Protection Initiative (SPI) under the direction of the Air Force Research Laboratory and the U.S. Department of Defense.
- It is designed to boot from a CD or USB pen drive on any Intel-based computer.
- LPS runs solely in memory and leaves no traces behind after use.
- Features include a smart card-enabled Firefox browser supporting Common Access Card (CAC) and Personal Identity Verification (PIV) cards, a PDF and text viewer, Java, and Encryption Wizard.
- It allows general web browsing and connecting to remote networks while ensuring that no trace of work activity (or malware) is written to the local computer.
- LPS is updated at least every quarter, and users are recommended to download a fresh copy with each update.
- The interface is simple, resembling Windows XP, and includes essential applications like Firefox, Leafpad, OpenSSH, and Citrix XenApp2.

Lightweight Portable Security - ArchiveOS
Web site: www.spi.dod.mil/lipose.htm (not active) Origin: USA Category: Security Desktop environment: Xfce Architecture: x86 Based on: Thinstation Wikipedia: Lightweight Portable Security Media: Live CD The last version | Released: 1.7.0 | July 20, 2016 Zobacz po polsku: Lightweight Portable...archiveos.org
