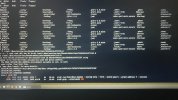
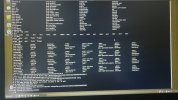
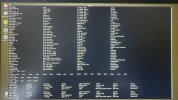
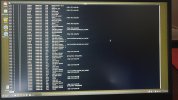
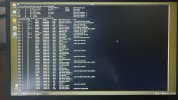
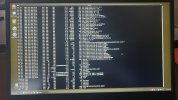
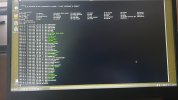
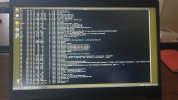
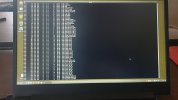
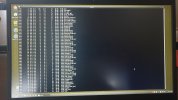
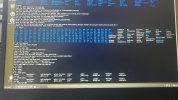
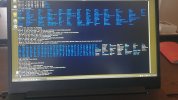
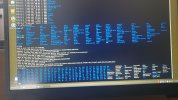
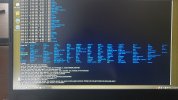
Hi all. I'll keep it short for starters. I'm writing on my phone as my laptop has been rendered useless by a trojan somewhere in preboot/firmware.
Basically I've seen it load a bundle of malicious scripts and binaries into /usr/share as readonly tmpfs and it symlinks everything in /sbin and /bin to busybox. There are scripts like fakeroot.sh and countless stuff that looks malicious from a mile away.
It seems to create a virtual environment as I can be browsing around looking at something suspicious and next time I ls I'm back in my home dir again. Unable to edit files owned by root as root user.
It seems to be a call-home type of deal. It sets up an smb server and a top server where it periodically uploads data first chance it gets. I've see logs where it crawls recent files and a list of excluded directories and sends it in litesql db format or similar down a socket which I assume which seems to be connected to one or many irq chls. Ive seen co figuration with thousands of irq chls of dubious nature like 'homeporn' and shit like that. Ah yes it fires up camera and mic and a remotemediaserverd or similar.
Even if my network interfaces are down its online with a fake dns server 127.0.0.53 which is connected to a socket on my local machine.
Ive been unable to extract an image to usb. When i try to write to usb using dd it wipes it immediately.
This has been ongoing for years and i have cross contaminated all my laptops with a dirty usb stick ithink.
Any pointers on how to get rid of this? The only place where im left alone is in the uefi shell.. I'll try to get some photo evidence but im 100% sure this is a platform independent boot sector virus. Its persisted over 30 attempts at wiping my disk. And ive tried 5 distros. Currently Fedora.
Basically I've seen it load a bundle of malicious scripts and binaries into /usr/share as readonly tmpfs and it symlinks everything in /sbin and /bin to busybox. There are scripts like fakeroot.sh and countless stuff that looks malicious from a mile away.
It seems to create a virtual environment as I can be browsing around looking at something suspicious and next time I ls I'm back in my home dir again. Unable to edit files owned by root as root user.
It seems to be a call-home type of deal. It sets up an smb server and a top server where it periodically uploads data first chance it gets. I've see logs where it crawls recent files and a list of excluded directories and sends it in litesql db format or similar down a socket which I assume which seems to be connected to one or many irq chls. Ive seen co figuration with thousands of irq chls of dubious nature like 'homeporn' and shit like that. Ah yes it fires up camera and mic and a remotemediaserverd or similar.
Even if my network interfaces are down its online with a fake dns server 127.0.0.53 which is connected to a socket on my local machine.
Ive been unable to extract an image to usb. When i try to write to usb using dd it wipes it immediately.
This has been ongoing for years and i have cross contaminated all my laptops with a dirty usb stick ithink.
Any pointers on how to get rid of this? The only place where im left alone is in the uefi shell.. I'll try to get some photo evidence but im 100% sure this is a platform independent boot sector virus. Its persisted over 30 attempts at wiping my disk. And ive tried 5 distros. Currently Fedora.