When running a swarm, there is a lot of information stored within the logs of the managing node. The information can be sensitive to security.
We store everything that is performed by the managing nodes in the logs. The head node creates the logs and replicates the logs to the other managers. Since each manager has a copy of the logs, then any manager can take the place as the leading node in the swarm if the leading node goes down.
The logs also store keys, passwords or any other type of secret information used on the swarm. The key is also present that is used to encrypt messages between the nodes in the swarm.
The logs are all encrypted, but if someone finds the key, then the logs can be unencrypted and read.
The lock will encrypt the keys to start the TLS communication between the nodes, as well as access the logs. Until the lock is 'unlocked', the swarm will not start.
So, we need to lock the logs to allow for more security. Basically, the swarm will not start until we provide the key whenever we start or restart the swarm.
NOTE: If your Docker system is critical to be active all the time, locking the service may not be a good idea. If the server or service goes down, someone has to unlock it to start it. It will not auto-start.
I know we created a swarm before, but let's look at it again, except we need to lock the swarm. You can see the original article here.
NOTE: If you have a swarm already, I will cover locking an existing swarm soon.
Locking the Swarm when Created
I will assume you have Docker installed from your repository. All systems can ping one another, so they can communicate with each other.
On the system 'Docker1', we will make this system the 'Leader'. The system will be the head manager. The Leader creates the logs and copies them to other managers.
On 'Docker1', you need it IP Address. You can use the command 'ip a' to find it. My systems have IP Addresses as follows:
Docker1 192.168.1.109
Docker2 192.168.1.156
Docker3 192.168.1.215
I use the following command to create the swarm and enable locking:
docker swarm init --advertise-addr 192.168.1.109 --autolock
We will get a token to allow nodes to join. Also, there will be a key for unlocking the swarm after a restart. We show both keys in Figure 1.
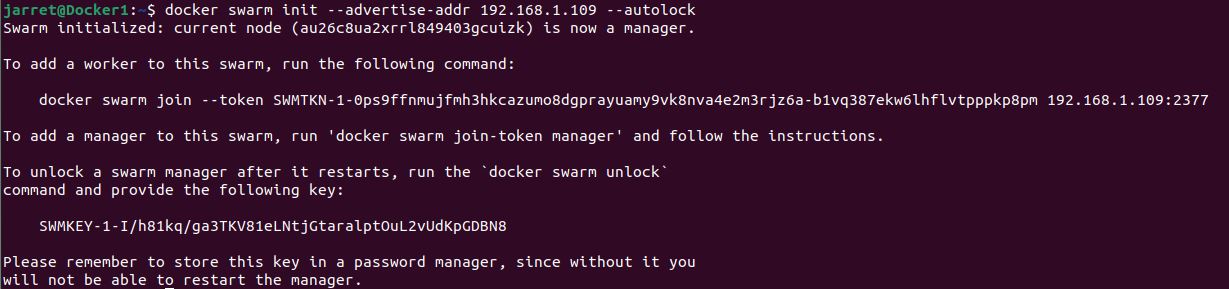
FIGURE 1
We should store the unlock key somewhere other than the local system for security.
If you run the command 'docker node ls' on Docker1, you can see that it is a single node in the swarm and is listed as the 'Leader'.
At this point, you can restart the service with 'sudo systemctl restart docker'. Once the service restarts, you can run 'docker node ls' and see that it is not running. You should receive the message 'Error response from daemon: Swarm is encrypted and needs to be unlocked before it can be used. Please use "docker swarm unlock" to unlock it.'.
So, to unlock the service, use the command 'docker swarm unlock' and, when prompted, enter the unlock key.
NOTE: If you lose the key, you can get again from any system that is a manager with the command 'docker swarm unlock-key' as long as you have already unlocked it.
Now, you need to add your nodes to your swarm.
Lock an Existing Swarm
In some cases, you may need to lock a swarm that has already been created. The process is similar and is only a single command.
We perform the command to lock the swarm on the 'Leader' and is 'docker swarm update –autolock=true'.
Once issued, it will give you the key, just like in Figure 2.
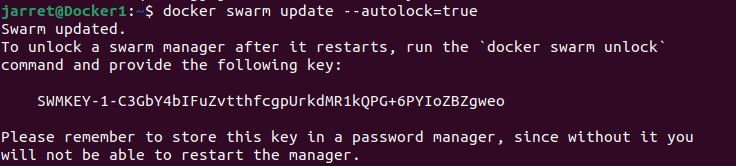
FIGURE 2
Again, keep this key somewhere safe and secure.
You can restart the docker service and see that it remains locked after the service starts. You'll need to enter the key to start the service with the command 'docker swarm unlock'.
Change Swarm Lock Key
There are two ways to change the key if you want or need to get a different key.
First, update the swarm and disable the 'autolock' with the command 'docker swarm update –autolock=false'. Once the lock is removed, you can enable it again by making the 'autolock=true', which will generate a new key.
Second, you can use the command 'docker swarm unlock-key --rotate'. If you have multiple managers in the swarm, you need to keep the old key for a bit. If another manager fails and restarts before the logs replicate to the managers, it will require the previous key to unlock it. The first way will also require you to keep the old key until everything is replicated as well.
Remove Lock from Swarm
I've already shown this before, but I'll go over it again because this can be important for a production server. I cannot emphasize enough that by locking the service, it will not auto-start without the unlock key. So, you may find that you do not want it to lock.
To remove the lock, you enter the command 'docker swarm update --autolock=false'. By disabling the feature, it will not be locked when the service restarts.
When removing the lock, you are not prompted to supply the key, since the service should be unlocked.
Conclusion
In some companies, it may be best to lock the Docker service to help provide more security for the information within Docker.
Locking the service provides more security for the Docker information that is in the logs and the communication key between the systems. Some companies have a high security mind when it comes to their information on the servers. Just be aware of the ability to lock down the Docker Service.
We store everything that is performed by the managing nodes in the logs. The head node creates the logs and replicates the logs to the other managers. Since each manager has a copy of the logs, then any manager can take the place as the leading node in the swarm if the leading node goes down.
The logs also store keys, passwords or any other type of secret information used on the swarm. The key is also present that is used to encrypt messages between the nodes in the swarm.
The logs are all encrypted, but if someone finds the key, then the logs can be unencrypted and read.
The lock will encrypt the keys to start the TLS communication between the nodes, as well as access the logs. Until the lock is 'unlocked', the swarm will not start.
So, we need to lock the logs to allow for more security. Basically, the swarm will not start until we provide the key whenever we start or restart the swarm.
NOTE: If your Docker system is critical to be active all the time, locking the service may not be a good idea. If the server or service goes down, someone has to unlock it to start it. It will not auto-start.
I know we created a swarm before, but let's look at it again, except we need to lock the swarm. You can see the original article here.
NOTE: If you have a swarm already, I will cover locking an existing swarm soon.
Locking the Swarm when Created
I will assume you have Docker installed from your repository. All systems can ping one another, so they can communicate with each other.
On the system 'Docker1', we will make this system the 'Leader'. The system will be the head manager. The Leader creates the logs and copies them to other managers.
On 'Docker1', you need it IP Address. You can use the command 'ip a' to find it. My systems have IP Addresses as follows:
Docker1 192.168.1.109
Docker2 192.168.1.156
Docker3 192.168.1.215
I use the following command to create the swarm and enable locking:
docker swarm init --advertise-addr 192.168.1.109 --autolock
We will get a token to allow nodes to join. Also, there will be a key for unlocking the swarm after a restart. We show both keys in Figure 1.
FIGURE 1
We should store the unlock key somewhere other than the local system for security.
If you run the command 'docker node ls' on Docker1, you can see that it is a single node in the swarm and is listed as the 'Leader'.
At this point, you can restart the service with 'sudo systemctl restart docker'. Once the service restarts, you can run 'docker node ls' and see that it is not running. You should receive the message 'Error response from daemon: Swarm is encrypted and needs to be unlocked before it can be used. Please use "docker swarm unlock" to unlock it.'.
So, to unlock the service, use the command 'docker swarm unlock' and, when prompted, enter the unlock key.
NOTE: If you lose the key, you can get again from any system that is a manager with the command 'docker swarm unlock-key' as long as you have already unlocked it.
Now, you need to add your nodes to your swarm.
Lock an Existing Swarm
In some cases, you may need to lock a swarm that has already been created. The process is similar and is only a single command.
We perform the command to lock the swarm on the 'Leader' and is 'docker swarm update –autolock=true'.
Once issued, it will give you the key, just like in Figure 2.
FIGURE 2
Again, keep this key somewhere safe and secure.
You can restart the docker service and see that it remains locked after the service starts. You'll need to enter the key to start the service with the command 'docker swarm unlock'.
Change Swarm Lock Key
There are two ways to change the key if you want or need to get a different key.
First, update the swarm and disable the 'autolock' with the command 'docker swarm update –autolock=false'. Once the lock is removed, you can enable it again by making the 'autolock=true', which will generate a new key.
Second, you can use the command 'docker swarm unlock-key --rotate'. If you have multiple managers in the swarm, you need to keep the old key for a bit. If another manager fails and restarts before the logs replicate to the managers, it will require the previous key to unlock it. The first way will also require you to keep the old key until everything is replicated as well.
Remove Lock from Swarm
I've already shown this before, but I'll go over it again because this can be important for a production server. I cannot emphasize enough that by locking the service, it will not auto-start without the unlock key. So, you may find that you do not want it to lock.
To remove the lock, you enter the command 'docker swarm update --autolock=false'. By disabling the feature, it will not be locked when the service restarts.
When removing the lock, you are not prompted to supply the key, since the service should be unlocked.
Conclusion
In some companies, it may be best to lock the Docker service to help provide more security for the information within Docker.
Locking the service provides more security for the Docker information that is in the logs and the communication key between the systems. Some companies have a high security mind when it comes to their information on the servers. Just be aware of the ability to lock down the Docker Service.

