Many businesses and organizations need ways to limit access to specific applications. Application Armor (AppArmor) can prevent apps from accessing specific folders or even the Internet.
AppArmor provides Mandatory Access Control (MAC). The MAC is a profile which is set up per program to restrict access to resources. The security feature allows you to prevent an application from gaining access to files, folders and the Internet. In a sense you can nearly sandbox a program.
The AppArmor service is installed and enabled by default on Ubuntu systems. Very little else is needed unless you want to create or modify profiles. Profiles allow you to lock down specific access for applications.
Verify the AppArmor Service
Since AppArmor is installed and enabled by default this section should have no bearing. Just in case the service was disabled or removed we will check to be safe.
You can run the following command to verify that AppArmor is installed and running:
The first line after you type in your password, if needed, should be a green dot followed by ‘apparmor.service - AppArmor initialization’. The green dot shows the service is active.
You can also use the command ‘systemctl status apparmor’ which will produce the same output.
If an error occurs then you may need to install AppArmor by using the following command:
To stop the AppArmor Service for any reason, which will also stop any enforced profiles, use the command:
Then to restart the service use:
Your service should be installed and running at this point and you can now secure applications with some additions.
AppArmor Additions
AppArmor by itself is not enough so you need to install some additions to give you more abilities to manage it. The first addition adds more profiles to AppArmor.
NOTE: A profile is a file containing the information about programs and what it can or cannot do in the Operating System (OS).
Once these are installed you should now have the files you need to manage AppArmor.
Let me list the applications we will be covering:
Now that we have a list of programs to use we can get into examples of using them.
AppArmor Usage
Let’s cover the basics of the AppArmor Profiles.
A Profile is used to specify the capabilities of a specific program. A Profile can be enabled or disabled. For any Profile that is enabled it can be placed into one of two modes:
Let’s look at activating and disabling AppArmor Profiles before we can set them to ‘complain’ or ‘enforce’.
If you run the command ‘sudo apparmor_status’ you will see a list of Profiles. The Profiles are listed first by those which are enforced. The end of the list dhows those which are in complain mode. The program then lists the running processes which are enforced and then those in complain mode.
Profiles are stored in the folder ‘/etc/apparmor.d’. Notice something about the Profiles. The file name is the location and program name separated by a period. For example, the Profile for Firefox is ‘usr.bin.firefox’. By default the Profile for Firefox is not enabled. If you look at the output from ‘apparmor_status’ you will see that Firefox is not listed. A Profile does exist so this means the Profile is not enabled.
To learn to enable a Profile we will enable the Firefox Profile.
The difference between an enabled and disabled profile is that in ‘/etc/apparmor.d’ there is a folder called ‘disable’. If a symbolic link is created of a profile in the disable folder then the profile is disabled.
Since Firefox is disabled we can enable it by removing the symbolic link. To remove the link you can use the following command:
If you remove the symbolic link you then need to have AppArmor reload the listing of Profiles. To reload the Profile listing you run the following command:
The ‘-a’ causes the program to add the specified Profile.
If you check the status with ‘sudo apparmor_status’ you should see that it is now set in ‘enforce’ mode.
We now have a Profile in enforce mode and we can change it to complain mode. To change a Profile to complain mode we use the following command:
Now if we check the status (sudo aa-status) we can see that Firefox is now in complain mode.
All we need to do now is to disable the Firefox Profile. To disable a Profile we need to recreate the symbolic link in the ‘/etc/apparmor.d/disable’ folder. To create the link use the following command:
Now that the link is made the AppArmor Service needs to remove the listing from its database. To remove the listing use the following command:
If you do not perform the last command then nothing will be changed until you perform the command or reboot the system causing the service to reload.
Now we can look at denying access for a program to the Internet and/or folders.
Denying Internet Access
Let’s look at a program that accesses the Internet such as Firefox. We need to enable it and then edit the Profile.
Once you have enabled the Profile you can open the Profile in your preferred editor.
After the file is opened in your editor you can search for the word ‘network’. You can see my result in Figure 1.
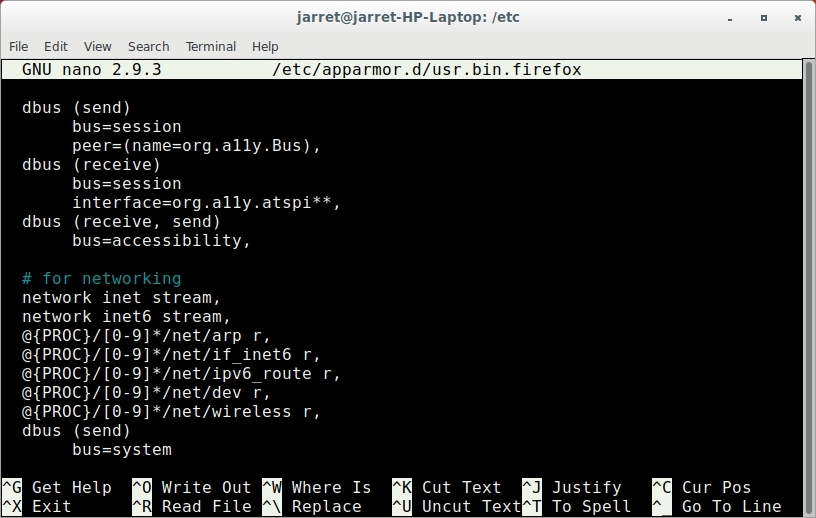
FIGURE 1
The first two lines allows streaming using IPv4 (inet) and IPv6 (inet6). What we will do is comment the two lines by placing a hashtag (#) at the beginning of those two lines.
To prohibit access to the Internet we need to add three lines as follows:
Save the file and reload the Profile with the command:
If the Profile is enabled you will need to remove and then reload it:
When you start Firefox you should not be able to access the Internet. You can either edit the Profile, disable it or put it in complain mode to restore Internet access to Firefox.
Denying Folder Access
In this example we will set up an application with limited access to folders. Also, we will create a Profile for the program when one does not exist.
In this example I will create a Profile for the text editor called Leafpad.
NOTE: Check the /etc/apparmor.d/ and make sure you do not have a Profile for the program you will be using. If a Profile exists for an app and you try to create one then you will receive an error. If you are going to use my example be sure you have Leafpad installed.
To create a new Profile you issue the command:
You will be prompted then to start the program you specified, in this case ‘leafpad’.
Once the program is started you need to perform the options you want to not allow a user to perform. Any folder or drive you want to disallow you need to access by opening a file on at that location. Specific files that you will deny access to should be opened as well. After you have accessed all of the necessary folders and files you can close ‘leafpad’.
Now you need to go back to the Terminal where the profile is waiting to be generated. Press the ‘S’ key to ‘Scan the systemlog for Apparmor events’ to start generating the Profile.
Each event will be displayed. Some may not make sense, but if it doesn’t then usually just press ‘A’ to allow the event. When you see a listing for a folder or file that you want to disallow access then press the ‘D’ key to deny access. After you get through the whole list of events you will then be prompted to press ‘S’ to ‘Save’ the Profile. Click ‘F’ to finish the Profile processing.
After you save the Profile it should be put into enforce mode.
NOTE: When you start to create a Profile a generic Profile is created and placed into complain mode. In complain mode all events are logged and this allows you to choose which are allowed or denied. After the choices are made the Profile is generated and placed in enforce mode.
In some cases you get an error and the Profile is left in complain mode. To fix this you need to edit the Profile and you need to remove the line ‘#include <abstractions/ubuntu-browsers.d/plugins-common>’. This line causes issues and once removed you can place the Profile into enforce mode.
If a Profile doesn’t quite work correctly you could try to edit the file or even delete it and start over.
Usage
The profiles can be copied between systems. Once a profile is created and edited to function the way you want it it can be copied to other systems.
Any profile can be edited later or even disabled once it is not needed.
For example, a Profile could limit Internet access on a kiosk so only local HTML files can be accessed.
Conclusion
AppArmor is a great way to limit access to the Internet or files/folders without having to change network settings or file/folder permissions.
AppArmor may require some practice to create necessary Profiles. Once you get the hang of creating Profiles it can be quite simple. Just keep practicing.
AppArmor provides Mandatory Access Control (MAC). The MAC is a profile which is set up per program to restrict access to resources. The security feature allows you to prevent an application from gaining access to files, folders and the Internet. In a sense you can nearly sandbox a program.
The AppArmor service is installed and enabled by default on Ubuntu systems. Very little else is needed unless you want to create or modify profiles. Profiles allow you to lock down specific access for applications.
Verify the AppArmor Service
Since AppArmor is installed and enabled by default this section should have no bearing. Just in case the service was disabled or removed we will check to be safe.
You can run the following command to verify that AppArmor is installed and running:
Code:
sudo service apparmor statusThe first line after you type in your password, if needed, should be a green dot followed by ‘apparmor.service - AppArmor initialization’. The green dot shows the service is active.
You can also use the command ‘systemctl status apparmor’ which will produce the same output.
If an error occurs then you may need to install AppArmor by using the following command:
Code:
sudo apt install apparmorTo stop the AppArmor Service for any reason, which will also stop any enforced profiles, use the command:
Code:
systemctl stop apparmorThen to restart the service use:
Code:
systemctl start apparmorYour service should be installed and running at this point and you can now secure applications with some additions.
AppArmor Additions
AppArmor by itself is not enough so you need to install some additions to give you more abilities to manage it. The first addition adds more profiles to AppArmor.
NOTE: A profile is a file containing the information about programs and what it can or cannot do in the Operating System (OS).
Code:
sudo apt install apparmor-utils apparmor-profilesOnce these are installed you should now have the files you need to manage AppArmor.
Let me list the applications we will be covering:
- apparmor_status – lists the status of all active profiles
- aa-complain – set a profile to complain mode
- aa-enforce – set a profile to enforce mode
- apparmor_parser – reload profile status
- aa-genprof – create a new profile
- aa-logprof – list profile errors for complain mode
Now that we have a list of programs to use we can get into examples of using them.
AppArmor Usage
Let’s cover the basics of the AppArmor Profiles.
A Profile is used to specify the capabilities of a specific program. A Profile can be enabled or disabled. For any Profile that is enabled it can be placed into one of two modes:
- Complain – the Profile is active but not following the specified rules. A log is kept of all broken rul
- Enforce – the Profile is active and the rules are active.
Let’s look at activating and disabling AppArmor Profiles before we can set them to ‘complain’ or ‘enforce’.
If you run the command ‘sudo apparmor_status’ you will see a list of Profiles. The Profiles are listed first by those which are enforced. The end of the list dhows those which are in complain mode. The program then lists the running processes which are enforced and then those in complain mode.
Profiles are stored in the folder ‘/etc/apparmor.d’. Notice something about the Profiles. The file name is the location and program name separated by a period. For example, the Profile for Firefox is ‘usr.bin.firefox’. By default the Profile for Firefox is not enabled. If you look at the output from ‘apparmor_status’ you will see that Firefox is not listed. A Profile does exist so this means the Profile is not enabled.
To learn to enable a Profile we will enable the Firefox Profile.
The difference between an enabled and disabled profile is that in ‘/etc/apparmor.d’ there is a folder called ‘disable’. If a symbolic link is created of a profile in the disable folder then the profile is disabled.
Since Firefox is disabled we can enable it by removing the symbolic link. To remove the link you can use the following command:
Code:
sudo rm /etc/apparmor.d/disable/usr.bin.firefoxIf you remove the symbolic link you then need to have AppArmor reload the listing of Profiles. To reload the Profile listing you run the following command:
Code:
sudo apparmor_parser -a /etc/apparmor.d/usr.bin.firefoxThe ‘-a’ causes the program to add the specified Profile.
If you check the status with ‘sudo apparmor_status’ you should see that it is now set in ‘enforce’ mode.
We now have a Profile in enforce mode and we can change it to complain mode. To change a Profile to complain mode we use the following command:
Code:
sudo aa-complain usr.bin.firefoxNow if we check the status (sudo aa-status) we can see that Firefox is now in complain mode.
All we need to do now is to disable the Firefox Profile. To disable a Profile we need to recreate the symbolic link in the ‘/etc/apparmor.d/disable’ folder. To create the link use the following command:
Code:
sudo ln -s /etc/apparmor.d/usr.bin.firefox /etc/apparmor.d/disable/Now that the link is made the AppArmor Service needs to remove the listing from its database. To remove the listing use the following command:
Code:
sudo apparmor_parser -R /etc/apparmor.d/usr.bin.firefoxIf you do not perform the last command then nothing will be changed until you perform the command or reboot the system causing the service to reload.
Now we can look at denying access for a program to the Internet and/or folders.
Denying Internet Access
Let’s look at a program that accesses the Internet such as Firefox. We need to enable it and then edit the Profile.
Once you have enabled the Profile you can open the Profile in your preferred editor.
After the file is opened in your editor you can search for the word ‘network’. You can see my result in Figure 1.
FIGURE 1
The first two lines allows streaming using IPv4 (inet) and IPv6 (inet6). What we will do is comment the two lines by placing a hashtag (#) at the beginning of those two lines.
To prohibit access to the Internet we need to add three lines as follows:
Code:
deny network inet,
deny network inet6,
deny network raw,Save the file and reload the Profile with the command:
Code:
sudo apparmor_parser -a /etc/apparmor.d/usr.bin.firefoxIf the Profile is enabled you will need to remove and then reload it:
Code:
sudo apparmor_parser -R /etc/apparmor.d/usr.bin.firefox
sudo apparmor_parser -a /etc/apparmor.d/usr.bin.firefoxWhen you start Firefox you should not be able to access the Internet. You can either edit the Profile, disable it or put it in complain mode to restore Internet access to Firefox.
Denying Folder Access
In this example we will set up an application with limited access to folders. Also, we will create a Profile for the program when one does not exist.
In this example I will create a Profile for the text editor called Leafpad.
NOTE: Check the /etc/apparmor.d/ and make sure you do not have a Profile for the program you will be using. If a Profile exists for an app and you try to create one then you will receive an error. If you are going to use my example be sure you have Leafpad installed.
To create a new Profile you issue the command:
Code:
sudo aa-genprof leafpadYou will be prompted then to start the program you specified, in this case ‘leafpad’.
Once the program is started you need to perform the options you want to not allow a user to perform. Any folder or drive you want to disallow you need to access by opening a file on at that location. Specific files that you will deny access to should be opened as well. After you have accessed all of the necessary folders and files you can close ‘leafpad’.
Now you need to go back to the Terminal where the profile is waiting to be generated. Press the ‘S’ key to ‘Scan the systemlog for Apparmor events’ to start generating the Profile.
Each event will be displayed. Some may not make sense, but if it doesn’t then usually just press ‘A’ to allow the event. When you see a listing for a folder or file that you want to disallow access then press the ‘D’ key to deny access. After you get through the whole list of events you will then be prompted to press ‘S’ to ‘Save’ the Profile. Click ‘F’ to finish the Profile processing.
After you save the Profile it should be put into enforce mode.
NOTE: When you start to create a Profile a generic Profile is created and placed into complain mode. In complain mode all events are logged and this allows you to choose which are allowed or denied. After the choices are made the Profile is generated and placed in enforce mode.
In some cases you get an error and the Profile is left in complain mode. To fix this you need to edit the Profile and you need to remove the line ‘#include <abstractions/ubuntu-browsers.d/plugins-common>’. This line causes issues and once removed you can place the Profile into enforce mode.
If a Profile doesn’t quite work correctly you could try to edit the file or even delete it and start over.
Usage
The profiles can be copied between systems. Once a profile is created and edited to function the way you want it it can be copied to other systems.
Any profile can be edited later or even disabled once it is not needed.
For example, a Profile could limit Internet access on a kiosk so only local HTML files can be accessed.
Conclusion
AppArmor is a great way to limit access to the Internet or files/folders without having to change network settings or file/folder permissions.
AppArmor may require some practice to create necessary Profiles. Once you get the hang of creating Profiles it can be quite simple. Just keep practicing.

