Security on a Linux system is very important for any Administrator or regular user. Security on home systems can be as important as a business server. Home systems can contain personal information that can be used for identity theft, credit card fraud, etc. Business servers can contain customer information which can be stolen and used in the same way.
How can one protect their system from outsiders?
One of the ways that outsiders get into a system is through software that they put on the Internet which is then downloaded and installed on systems. The software program contains a some type of malware which allows other users access to your information.
Beta software could contain bugs which will inadvertently cause system instability. By installing faulty software you can cause more system failures and crashes.
How can you limit access of certain software from causing possible issues that we mentioned? By running these applications in a sandbox you can prevent harming your Operating System (OS).
Sandbox
The Sandbox is a restricted area for running a process. The process is kept from accessing all of the system resources.
The process in question will not be able to perform malicious intentions if it should have any. Testing can be done to verify that the application will function normally without causing system issues like instability.
The limited access to memory, disk storage, etc can keep your other data safe from being stolen, erased or modified (ransomware).
You can kind of think of the Sandbox as its own little world within the Host System. It can easily be thought of as a ‘virtual system’ without having to install a whole OS in a program such as VirtualBox.
The ability of FireJail is that it uses the Linux SUID to limit the system access.
SUID
The ‘Set owner User ID (SUID)’ is used to allow anyone to execute a program with the privileges of the owner.
The Owner and Other users need Execute (X) access to the file. You can then add the SUID by using the command ‘sudo chmod u+s filename’ from the command-line. Since ‘Other’ has executable privileges to the file and your account is not the owner you are allowed to execute the file with the same privileges as the owner.
NOTE: For more information on SUID and file permissions see the article at https://linux.org/threads/lfcs-–-file-permissions.21498/#post-63113.
FireJail
Firejail is a program which allows you run another program in a sandbox by using Linux SUID permissions.
Let’s get the program installed and see how this works.
In a Terminal window you can use the following command to get Firejail installed:
Once Firejail is installed it has no settings for any programs. Firejail comes with numerous configuration files for various programs. The profiles are stored at ‘/etc/firejail’ after the install. You can use these profiles or create your own. You can start with the installed profiles and change these as needed. To do this you need to copy them to the folder ‘/~/.config/firejail/’. Before you copy the profiles you need to create the target folder and copy the profiles as follows:
To get Firejail to integrate with your Desktop (if you have one) of existing applications then run the command:
The command will remove any Firejail symlinks which may already exist. The program then scans your system for specific applications and sets up a symlink. Anytime the program is run it will automatically be in Firejail. If you do not want this to happen then do no execute the command. You can simply run an application in Firejail with the command:
If a specific profile does not exist for a program then Firejail will use a basic profile which may be very restrictive.
NOTE: If you want to remove all symlinks then execute the command ‘sudo firecfg --clean’. If you have a sound issue with a program then try the command ‘sudo firecfg --fix-sound’.
If you have an application which has no profile and you want to make one you can do the following things. You will need to create a profile, but you may want to start with a ‘generic’ profile. Find the name of the application and copy the ‘default.profile’ to ‘application-name.profile’. Make sure the application name is correct and proper case. You will then want to edit the new profile with a text editor.
Within the file is what will be allowed and now allowed by the program when it is run. The beginning of the profile lists ‘local’ files which are included with the contents of the profile. If you have items you want to be in every profile then you would put them in the file ‘/etc/firejail/default.local’.
The next section contains the include (inc) files. These files include all the needed information for each program when it is installed.
The following section of ‘default.profile’ are some cryptic lines which may not make sense. These lines are described in the ‘man 5 firejail-profile’ information and are described as follows:
The next section deals more with the filesystem. The entries are:
These are a few of the entries which can be used in the profiles. Again, you can use hashtags to enable or disable an entry. You can limit a running application quite a bit.
There is also a Graphical User Interface (GUI) for Firejail called Firetools which can be found at https://sourceforge.net/projects/firejail/files/firetools/. After installing it you should have a ‘Firetools Configuration Wizard’ under ‘Accessories’ and ‘Firetools’ under ‘Administration’.
Once installed you can run ‘Firejail Configuration Wizard’ to create your own profile. Let’s look at this a bit.
Firejail Configuration Wizard
Once started you should see a program similar to that in Figure 1.
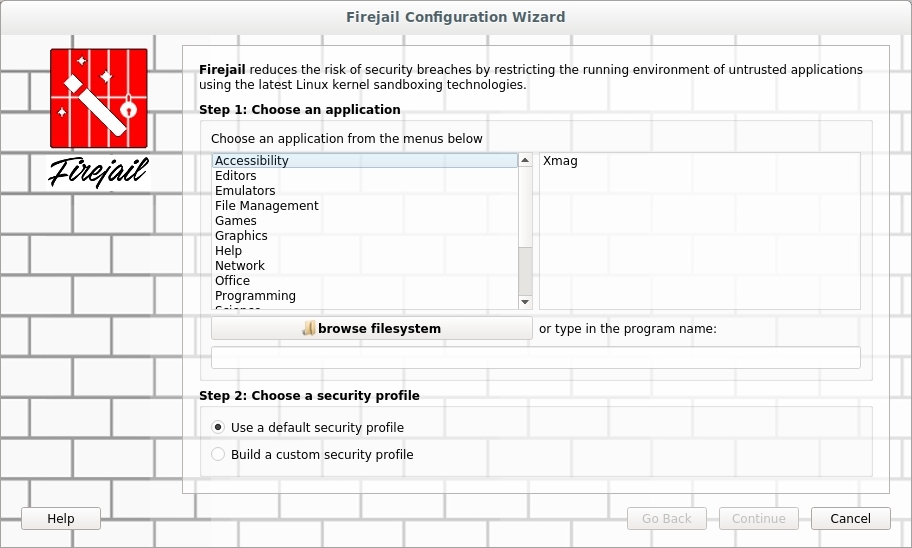
FIGURE 1
I used the ‘browse filesystem’ button to find a program I wrote in Gambas. I then selected the option to ‘Build a custom security profile’ before I clicked ‘Continue’.
The next screen, Figure 2, allows me to choose the filesystem restrictions. I will allow access to the HOME folder as well as the TMP folder. I can also ‘Disable networking’ and then click ‘Continue’.
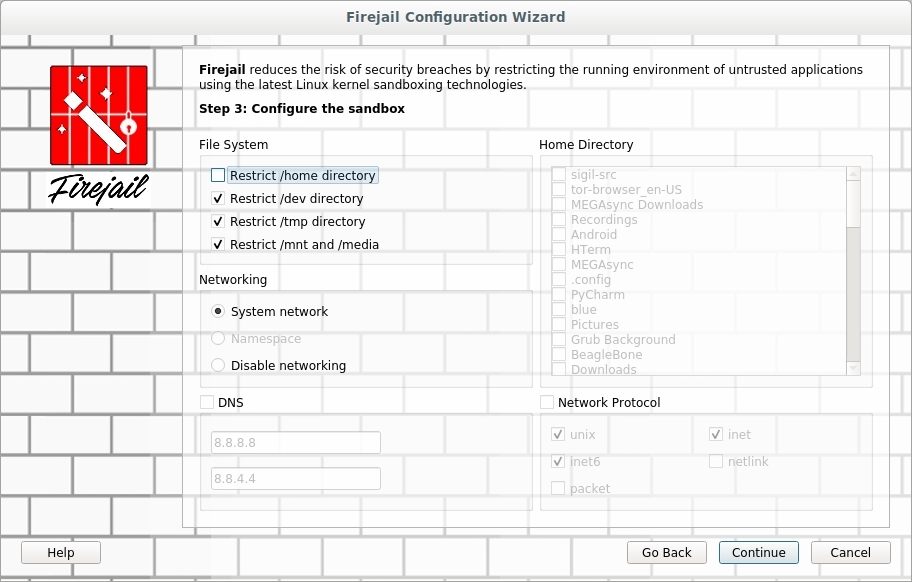
FIGURE 2
The third window allows me to restrict ‘Multimedia’ and ‘Kernel’ abilities from the program in Firejail. The third screen is shown in Figure 3.
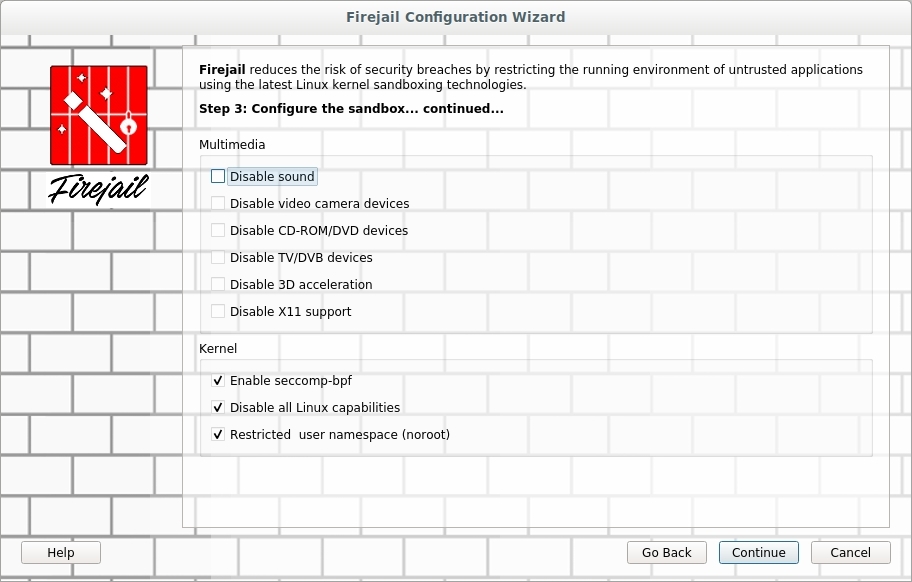
FIGURE 3
The last screen is one which you can perform monitoring and statistics as shown in Figure 4.
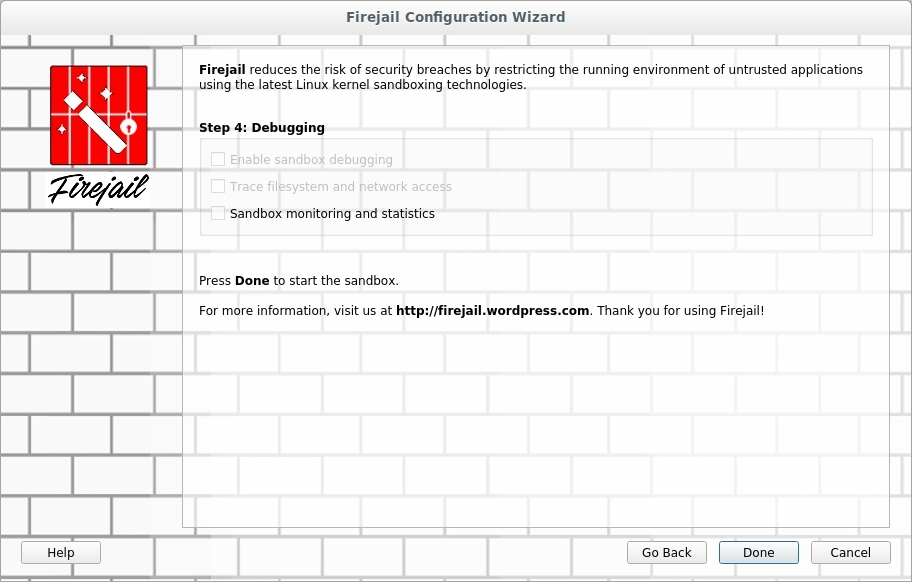
FIGURE 4
Once all settings are the way you want them you can click ‘Done’ to complete the configuration. Once you click ‘Done’ the application you selected should be launched.
If you want to see which applications are currently running in Firejail then you need to open ‘Firetools’. Once the program is started a window should appear with any apps you have installed on the Firetools menu. Right-click on the window and from the drop-down options select ‘Tools’. A new window should appear similar to the one in Figure 5.
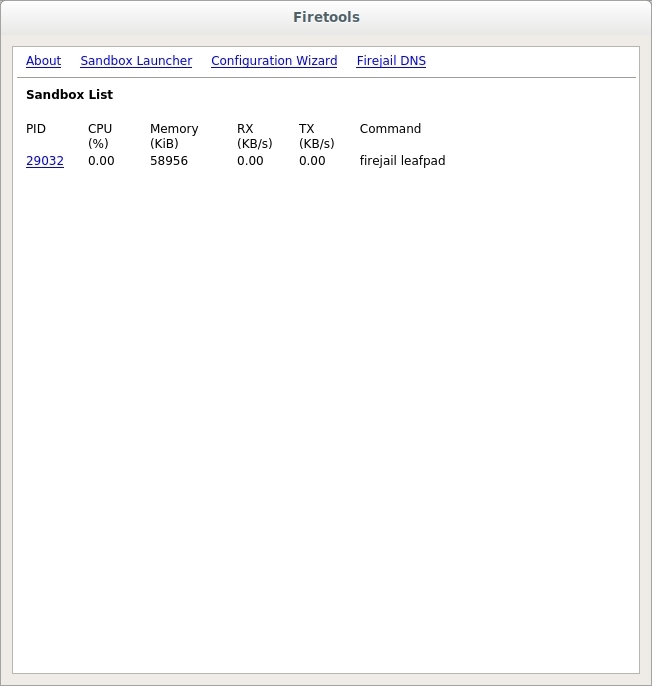
FIGURE 5
Conclusion
You should have basic understanding of using Firejail. Be sure to look over the MAN pages. Practice a bit with the profiles and even using the Firetool Configuration Wizard.
I hope this can help you create a secure sandbox in which to test programs.
How can one protect their system from outsiders?
One of the ways that outsiders get into a system is through software that they put on the Internet which is then downloaded and installed on systems. The software program contains a some type of malware which allows other users access to your information.
Beta software could contain bugs which will inadvertently cause system instability. By installing faulty software you can cause more system failures and crashes.
How can you limit access of certain software from causing possible issues that we mentioned? By running these applications in a sandbox you can prevent harming your Operating System (OS).
Sandbox
The Sandbox is a restricted area for running a process. The process is kept from accessing all of the system resources.
The process in question will not be able to perform malicious intentions if it should have any. Testing can be done to verify that the application will function normally without causing system issues like instability.
The limited access to memory, disk storage, etc can keep your other data safe from being stolen, erased or modified (ransomware).
You can kind of think of the Sandbox as its own little world within the Host System. It can easily be thought of as a ‘virtual system’ without having to install a whole OS in a program such as VirtualBox.
The ability of FireJail is that it uses the Linux SUID to limit the system access.
SUID
The ‘Set owner User ID (SUID)’ is used to allow anyone to execute a program with the privileges of the owner.
The Owner and Other users need Execute (X) access to the file. You can then add the SUID by using the command ‘sudo chmod u+s filename’ from the command-line. Since ‘Other’ has executable privileges to the file and your account is not the owner you are allowed to execute the file with the same privileges as the owner.
NOTE: For more information on SUID and file permissions see the article at https://linux.org/threads/lfcs-–-file-permissions.21498/#post-63113.
FireJail
Firejail is a program which allows you run another program in a sandbox by using Linux SUID permissions.
Let’s get the program installed and see how this works.
In a Terminal window you can use the following command to get Firejail installed:
Code:
sudo apt install firejail -yOnce Firejail is installed it has no settings for any programs. Firejail comes with numerous configuration files for various programs. The profiles are stored at ‘/etc/firejail’ after the install. You can use these profiles or create your own. You can start with the installed profiles and change these as needed. To do this you need to copy them to the folder ‘/~/.config/firejail/’. Before you copy the profiles you need to create the target folder and copy the profiles as follows:
Code:
cd ~
mkdir ~/.config/firejail
cp /etc/firejail/* ~/.config/firejail/To get Firejail to integrate with your Desktop (if you have one) of existing applications then run the command:
Code:
sudo firecfgThe command will remove any Firejail symlinks which may already exist. The program then scans your system for specific applications and sets up a symlink. Anytime the program is run it will automatically be in Firejail. If you do not want this to happen then do no execute the command. You can simply run an application in Firejail with the command:
Code:
firejail <program name>If a specific profile does not exist for a program then Firejail will use a basic profile which may be very restrictive.
NOTE: If you want to remove all symlinks then execute the command ‘sudo firecfg --clean’. If you have a sound issue with a program then try the command ‘sudo firecfg --fix-sound’.
If you have an application which has no profile and you want to make one you can do the following things. You will need to create a profile, but you may want to start with a ‘generic’ profile. Find the name of the application and copy the ‘default.profile’ to ‘application-name.profile’. Make sure the application name is correct and proper case. You will then want to edit the new profile with a text editor.
Within the file is what will be allowed and now allowed by the program when it is run. The beginning of the profile lists ‘local’ files which are included with the contents of the profile. If you have items you want to be in every profile then you would put them in the file ‘/etc/firejail/default.local’.
The next section contains the include (inc) files. These files include all the needed information for each program when it is installed.
The following section of ‘default.profile’ are some cryptic lines which may not make sense. These lines are described in the ‘man 5 firejail-profile’ information and are described as follows:
- caps.drop all - blacklists all Linux capabilities
- ipc-namespace - enable IPC namespace
- netfilter - if a new network namespace is made then use the default network filter
- no3d - disable 3D hardware acceleration
- nodvd - disables DVD and audio devices
- nogroups - disables use of groups
- nonewprivs - child processes will not get different privileges
- noroot - uses a user namespace and not root
- nosound - disables the sound system
- notv - disable DVB (Digital Video Broadcasting) TV devices
- novideo - disables video devices
- protocol unix,inet,inet6 - enables the listed protocols
- seccomp - enables or disables Secure Computing (seccomp) filters
- shell none - runs the program without a shell
The next section deals more with the filesystem. The entries are:
- disable-mnt - disable access to /mnt, /media, /run/mount and /run/media
- private - create and mount a new /root and /home/user folders which are deleted when program is closed
- private-bin program - create a new /bin folder which is mounted over /sbin, /usr/bin and /usr/sbin
- private-dev - create a new /dev folder which allows access to dri, null, full, zero, tty, pts, ptmx, random, urandom, log and shm
- private-etc none - build a new /etc with folders and files in list (none will copy; no files/folders)
- private-lib - makes a new /lib folder and copies files into it needed by application
- private-tmp - mount an extra temporary folder on top of /tmp
- memory-deny-write-execute - blocks attempts to make memory mappings that are writable and executable
- noexec ${HOME} - remounts the HOME folder with no execution abilities
- noexec /tmp - no execution of file in /tmp
These are a few of the entries which can be used in the profiles. Again, you can use hashtags to enable or disable an entry. You can limit a running application quite a bit.
There is also a Graphical User Interface (GUI) for Firejail called Firetools which can be found at https://sourceforge.net/projects/firejail/files/firetools/. After installing it you should have a ‘Firetools Configuration Wizard’ under ‘Accessories’ and ‘Firetools’ under ‘Administration’.
Once installed you can run ‘Firejail Configuration Wizard’ to create your own profile. Let’s look at this a bit.
Firejail Configuration Wizard
Once started you should see a program similar to that in Figure 1.
FIGURE 1
I used the ‘browse filesystem’ button to find a program I wrote in Gambas. I then selected the option to ‘Build a custom security profile’ before I clicked ‘Continue’.
The next screen, Figure 2, allows me to choose the filesystem restrictions. I will allow access to the HOME folder as well as the TMP folder. I can also ‘Disable networking’ and then click ‘Continue’.
FIGURE 2
The third window allows me to restrict ‘Multimedia’ and ‘Kernel’ abilities from the program in Firejail. The third screen is shown in Figure 3.
FIGURE 3
The last screen is one which you can perform monitoring and statistics as shown in Figure 4.
FIGURE 4
Once all settings are the way you want them you can click ‘Done’ to complete the configuration. Once you click ‘Done’ the application you selected should be launched.
If you want to see which applications are currently running in Firejail then you need to open ‘Firetools’. Once the program is started a window should appear with any apps you have installed on the Firetools menu. Right-click on the window and from the drop-down options select ‘Tools’. A new window should appear similar to the one in Figure 5.
FIGURE 5
Conclusion
You should have basic understanding of using Firejail. Be sure to look over the MAN pages. Practice a bit with the profiles and even using the Firetool Configuration Wizard.
I hope this can help you create a secure sandbox in which to test programs.

