Sometimes an NMAP scan can take some time or even perform more scans than needed. Some network administrators may have packet sniffers running on a network to alert them when certain activities are occurring. Because of these issues it is best to limit the amount scanning being performed. Keep these parameters in mind when scanning systems on a network.
Ports
Let’s start by setting the ports being scanned. To specify Ports in a scan you can use the parameter ‘-p [ports]’.
If we wanted to scan a whole subnet and test the systems to see if the SSH Login Port is enabled, we can perform the following command:
nmap <ip-address/subnet> -p <ports>
If I wanted to test for the SSH Port (22) for TCP on my network (192.168.0.1/24) then I would use the command:
sudo 192.168.0.1/24 -p 22
For my network I would get the results as shown in Figure 1.
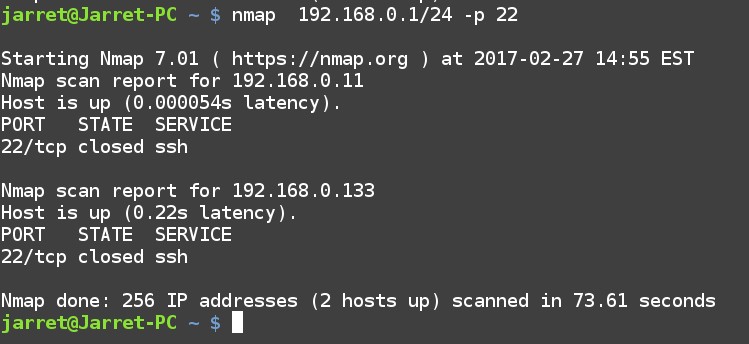
FIGURE 1
Multiple ports can be specified by separating the numbers with commas or a range by using a dash. For instance, to scan ports 21, 80 and 133 the port parameter would be ‘-p 21, 80, 133’. To test the range of ports from 100-150 the port parameter would be ‘-p 100-150’.
What if we wanted to scan a network for devices which accepts print jobs? A system accepting a print job can either be a Print Server (shared printer attached to a system) or a stand-alone printer with a network device. To check these on a network we can scan for Port 631 (CUPS – Common UNIX Printing System) or Port 515 (LPR – Line Printer Daemon). The command to scan for these on my network is:
nmap 192.168.0.1/24 -p 515, 631
The results of the scan are shown in Figure 2. You can see that a system at 192.168.0.11 has the port closed which is a system that is enabled to print, but not currently printing. The second system at 192.168.0.133 is a network printer which has the port opened and ready to receive a print job.
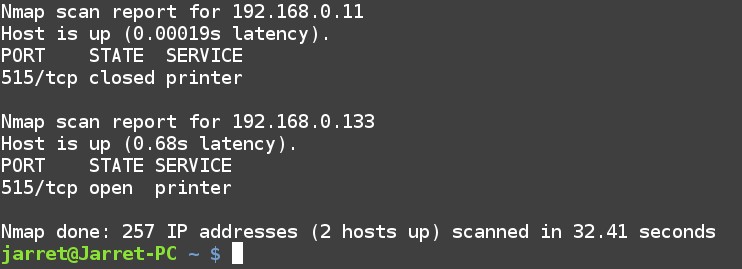
FIGURE 2
Scans can also be performed with the default Port name. Port names can be found in the file ‘/usr/share/nmap/nmap-services’. Use a command such as ‘more /usr/share/nmap/nmap-services’ to view it. In the file you can see that the SSH Port (22) has three entries:
ssh 22/sctp 0.000000 # Secure Shell Login
ssh 22/tcp 0.182286 # Secure Shell Login
ssh 22/udp 0.003905 # Secure Shell Login
If you wish to scan all three ports for SSH Ports open on your network you cannot simply use the commands:
nmap 192.168.0.1/24 -p 22
nmap 192.168.0.1/24 -p ssh
(these commands will only scan the TCP Ports not UDP or SCTP)
The command would be:
nmap 192.168.0.1/24 -p T:22,U:22,S:22
Make sure the options are separated by commas and not spaces or the last two options will be disregarded.
The test for open printer Ports can be performed for both TCP and UDP as shown in the following command:
nmap 192.168.0.1/24 -p T:515,631,U:515,631
The results of the scan can be seen in Figure 3.
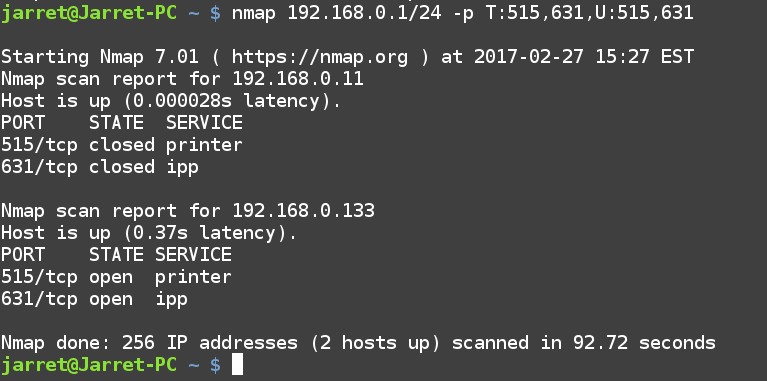
FIGURE 3
Exclude Addresses
Some subnets can contain a lot of systems and you may not want to scan every system on the network. Addresses can be excluded from the scan to make the scan faster and cut down on the amount of network traffic being generated.
To exclude addresses you can specify the address with the parameter ‘--exclude’. The options added to the parameter can be separated by commas.
It is possible to perform a ping command (-sP) to check active systems on a network can have exclusions. To check the network ‘192.168.0.1/24’ and exclude addresses ‘192.168.0.11,192.168.0.12’ would be:
nmap 192.168.0.1/24 -sP --exclude 192.168.0.11,192.168.0.12
If I wanted to exclude a range of 192.168.0.1-192.168.0.150 then the command would be:
nmap 192.168.0.1/24 -sP --exclude 192.168.0.1-192.168.0.150
In Figure 4 you can see that the IP Addresses scanned started at Address 192.168.0.151.
FIGURE 4
An exclude list can actually come from a list of IP Addresses to exclude from the scan. A text file can be made with each IP Address exclusion on a separate line, delimited by tabs or spaces. To use an exclusion list you need to use the parameter ‘--excludefile <filename>’.
For example, to use a file of IP Addresses to exclude which is called ‘exclusions’ the command would be:
nmap 192.168.0.1/24 -sP --excludefile /home/jarret/exclusion
NOTE: Make sure the full path to the exclusion file is used. The file name can be any valid filename.
Include Addresses
In some cases you may want to list the target IP Addresses to scan on a network. The IP Address to include in the scan can be very important also.
The included IP Addresses will come from a file and is used with the parameter ‘-iL’ followed by the filename to use.
For example, if I had a file called ‘inclusions’ I can include the file with the following command:
nmap 192.168.0.1/24 -sP -iL /home/jarret/inclusions
Just as with the Exclusions list the IP Addresses are on a separate line delimited by tabs or spaces.
You can also use both exclusions and inclusions at once. If an IP Address is in both the exclusion and inclusion list the address will be excluded. The exclusions have priority over the inclusions.
Fast Scan
To perform a fast scan of only specified Ports a text file can be used. The default Port list is at ‘/usr/share/nmap/nmap-services’ If you want to use your own you should rename the existing file and replace it with your own.
NOTE: Do NOT lose the original ‘nmap-services’ file. Always have a backup of the file.
I replaced the ‘nmap-services’ file, after backing up the original file, and the file included the following lines:
printer 515/tcp # spooler (lpd)
printer 515/udp # spooler (lpd)
ipp 631/tcp # Internet Printing Protocol
ipp 631/udp # Internet Printing Protocol
Of course with this small list I can easily use the Port (-p) parameter, but this is only as an example. The command to run the scan is:
nmap -F 192.168.0.1/24 --datadir /usr/share/nmap/nmap-services
The scan took about 39 seconds to scan the whole subnet. If you want to search for every Port in the original ‘nmap-services’ file then do not replace it and use it.
NOTE: To rename, erase or copy a file to the folder ‘usr/share/nmap’ requires Root privileges.
Source Port
The final parameter to keep in mind is to specify the Source Port from which the scan packets are being sent. You may wonder why this can be important. If you are trying to scan a system behind a Firewall then only certain Ports can be used to pass packets through the Firewall.
If you find a Firewall which has a Port open then you can send packets into the Firewall using that Port.
The parameter is ‘--source-port <port-number>’. For instance, if you wanted to use Port 80 the parameter would be ‘--source-port 80’.
Try a few scans and get some practice using these parameters with previous commands from other articles about NMAP. Get to know these parameters and how they work.
Happy scanning!
Ports
Let’s start by setting the ports being scanned. To specify Ports in a scan you can use the parameter ‘-p [ports]’.
If we wanted to scan a whole subnet and test the systems to see if the SSH Login Port is enabled, we can perform the following command:
nmap <ip-address/subnet> -p <ports>
If I wanted to test for the SSH Port (22) for TCP on my network (192.168.0.1/24) then I would use the command:
sudo 192.168.0.1/24 -p 22
For my network I would get the results as shown in Figure 1.
FIGURE 1
Multiple ports can be specified by separating the numbers with commas or a range by using a dash. For instance, to scan ports 21, 80 and 133 the port parameter would be ‘-p 21, 80, 133’. To test the range of ports from 100-150 the port parameter would be ‘-p 100-150’.
What if we wanted to scan a network for devices which accepts print jobs? A system accepting a print job can either be a Print Server (shared printer attached to a system) or a stand-alone printer with a network device. To check these on a network we can scan for Port 631 (CUPS – Common UNIX Printing System) or Port 515 (LPR – Line Printer Daemon). The command to scan for these on my network is:
nmap 192.168.0.1/24 -p 515, 631
The results of the scan are shown in Figure 2. You can see that a system at 192.168.0.11 has the port closed which is a system that is enabled to print, but not currently printing. The second system at 192.168.0.133 is a network printer which has the port opened and ready to receive a print job.
FIGURE 2
Scans can also be performed with the default Port name. Port names can be found in the file ‘/usr/share/nmap/nmap-services’. Use a command such as ‘more /usr/share/nmap/nmap-services’ to view it. In the file you can see that the SSH Port (22) has three entries:
ssh 22/sctp 0.000000 # Secure Shell Login
ssh 22/tcp 0.182286 # Secure Shell Login
ssh 22/udp 0.003905 # Secure Shell Login
If you wish to scan all three ports for SSH Ports open on your network you cannot simply use the commands:
nmap 192.168.0.1/24 -p 22
nmap 192.168.0.1/24 -p ssh
(these commands will only scan the TCP Ports not UDP or SCTP)
The command would be:
nmap 192.168.0.1/24 -p T:22,U:22,S:22
Make sure the options are separated by commas and not spaces or the last two options will be disregarded.
The test for open printer Ports can be performed for both TCP and UDP as shown in the following command:
nmap 192.168.0.1/24 -p T:515,631,U:515,631
The results of the scan can be seen in Figure 3.
FIGURE 3
Exclude Addresses
Some subnets can contain a lot of systems and you may not want to scan every system on the network. Addresses can be excluded from the scan to make the scan faster and cut down on the amount of network traffic being generated.
To exclude addresses you can specify the address with the parameter ‘--exclude’. The options added to the parameter can be separated by commas.
It is possible to perform a ping command (-sP) to check active systems on a network can have exclusions. To check the network ‘192.168.0.1/24’ and exclude addresses ‘192.168.0.11,192.168.0.12’ would be:
nmap 192.168.0.1/24 -sP --exclude 192.168.0.11,192.168.0.12
If I wanted to exclude a range of 192.168.0.1-192.168.0.150 then the command would be:
nmap 192.168.0.1/24 -sP --exclude 192.168.0.1-192.168.0.150
In Figure 4 you can see that the IP Addresses scanned started at Address 192.168.0.151.
FIGURE 4
An exclude list can actually come from a list of IP Addresses to exclude from the scan. A text file can be made with each IP Address exclusion on a separate line, delimited by tabs or spaces. To use an exclusion list you need to use the parameter ‘--excludefile <filename>’.
For example, to use a file of IP Addresses to exclude which is called ‘exclusions’ the command would be:
nmap 192.168.0.1/24 -sP --excludefile /home/jarret/exclusion
NOTE: Make sure the full path to the exclusion file is used. The file name can be any valid filename.
Include Addresses
In some cases you may want to list the target IP Addresses to scan on a network. The IP Address to include in the scan can be very important also.
The included IP Addresses will come from a file and is used with the parameter ‘-iL’ followed by the filename to use.
For example, if I had a file called ‘inclusions’ I can include the file with the following command:
nmap 192.168.0.1/24 -sP -iL /home/jarret/inclusions
Just as with the Exclusions list the IP Addresses are on a separate line delimited by tabs or spaces.
You can also use both exclusions and inclusions at once. If an IP Address is in both the exclusion and inclusion list the address will be excluded. The exclusions have priority over the inclusions.
Fast Scan
To perform a fast scan of only specified Ports a text file can be used. The default Port list is at ‘/usr/share/nmap/nmap-services’ If you want to use your own you should rename the existing file and replace it with your own.
NOTE: Do NOT lose the original ‘nmap-services’ file. Always have a backup of the file.
I replaced the ‘nmap-services’ file, after backing up the original file, and the file included the following lines:
printer 515/tcp # spooler (lpd)
printer 515/udp # spooler (lpd)
ipp 631/tcp # Internet Printing Protocol
ipp 631/udp # Internet Printing Protocol
Of course with this small list I can easily use the Port (-p) parameter, but this is only as an example. The command to run the scan is:
nmap -F 192.168.0.1/24 --datadir /usr/share/nmap/nmap-services
The scan took about 39 seconds to scan the whole subnet. If you want to search for every Port in the original ‘nmap-services’ file then do not replace it and use it.
NOTE: To rename, erase or copy a file to the folder ‘usr/share/nmap’ requires Root privileges.
Source Port
The final parameter to keep in mind is to specify the Source Port from which the scan packets are being sent. You may wonder why this can be important. If you are trying to scan a system behind a Firewall then only certain Ports can be used to pass packets through the Firewall.
If you find a Firewall which has a Port open then you can send packets into the Firewall using that Port.
The parameter is ‘--source-port <port-number>’. For instance, if you wanted to use Port 80 the parameter would be ‘--source-port 80’.
Try a few scans and get some practice using these parameters with previous commands from other articles about NMAP. Get to know these parameters and how they work.
Happy scanning!
Last edited:

