So, after having completely wiped, sanitized both my drives and clean install, it took only about 1.5 hours for it to re/establish itself with full force. Thats 1.4 hours longer than usual though, but still. ESET smart security scanner said it\s an UEFI variant of CompuTrace, so its not only a virus, but a remote hacker implementing an uefi virus/hijacking the uefi.
I thought of a few solution and at the moment one of them is working quite well.
1. I pulled out the wifi card from laptop, I dont want wifi or bluetooth near my life ever again, so those two are gone, feels good.
2. I encrypted an ubuntu live usb along with fully encrypting my two hard drives. No matter how much UEFI this virus is hijacking, it has no power unless it can be supplemented by an OS. So im using Virtualbox within the bootable ubuntu while the two drives are full encrypted, so far i have not seen a trace of any hacker or virus for many hours. Im not going to say its a success until at least a week or more has gone though. Kind of silly, but funny.
The other option was to re-claim the UEFI using Chipsec, but it seemed very risky and also quite complicated as im still only like 5 days in to using linux overall, I feel im too old to learn new things, I get super frustrated by how hard it is to just install something in comparison to windows, there is no double clicking and let it run, well sometimes I guess but for the most part you need to install 7 different dependencies in terminal just to launch one single app, like qtorrent or similar. I know, the benefits outweighs the cons long term most likely and Im just being grumpy.
The security and overall free hands you have in linux seems vastly much better than windows. I feel like I have much better overview of whats going on with my connection, using the netplan/connection manager, as well as being able to very simply block ports, the rdp port and ssh port got blocked real quick.
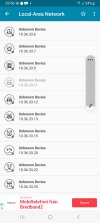
Other than that, Ill throw in a question if anyone can or wants to answer, is there a particular piece of hardware that should be replaced if it goes wrong? I feel like its going to be hard to find someone to flash the SPI physically and rather just replace some pieces as cheap as possible. Rather not buy a new computer either until I know my home is secured, because I actually believe my neighbors are hacked pretty hard and its been using those connections to get to me as well. Ive seen their routers in use frequently in my network during my "battles"
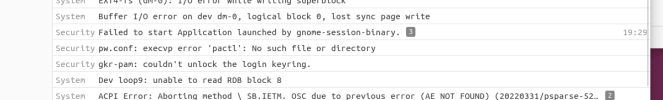
Some screenshots as well, the gkpam and exec thing was from the hacker/virus, have not seen anything from it since.
I thought of a few solution and at the moment one of them is working quite well.
1. I pulled out the wifi card from laptop, I dont want wifi or bluetooth near my life ever again, so those two are gone, feels good.
2. I encrypted an ubuntu live usb along with fully encrypting my two hard drives. No matter how much UEFI this virus is hijacking, it has no power unless it can be supplemented by an OS. So im using Virtualbox within the bootable ubuntu while the two drives are full encrypted, so far i have not seen a trace of any hacker or virus for many hours. Im not going to say its a success until at least a week or more has gone though. Kind of silly, but funny.
The other option was to re-claim the UEFI using Chipsec, but it seemed very risky and also quite complicated as im still only like 5 days in to using linux overall, I feel im too old to learn new things, I get super frustrated by how hard it is to just install something in comparison to windows, there is no double clicking and let it run, well sometimes I guess but for the most part you need to install 7 different dependencies in terminal just to launch one single app, like qtorrent or similar. I know, the benefits outweighs the cons long term most likely and Im just being grumpy.
The security and overall free hands you have in linux seems vastly much better than windows. I feel like I have much better overview of whats going on with my connection, using the netplan/connection manager, as well as being able to very simply block ports, the rdp port and ssh port got blocked real quick.
Other than that, Ill throw in a question if anyone can or wants to answer, is there a particular piece of hardware that should be replaced if it goes wrong? I feel like its going to be hard to find someone to flash the SPI physically and rather just replace some pieces as cheap as possible. Rather not buy a new computer either until I know my home is secured, because I actually believe my neighbors are hacked pretty hard and its been using those connections to get to me as well. Ive seen their routers in use frequently in my network during my "battles"
Some screenshots as well, the gkpam and exec thing was from the hacker/virus, have not seen anything from it since.