From their website, "WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPsec, while avoiding the massive headache."
Installing Wireguard is a straightforward procedure. Start by installing the Linux header files for your kernel using the following command :
The results of ‘$(uname -r)’ fill in the current kernel version. Make sure the current running kernel is the version you want to be using for Wireguard.
Now you can install Wireguard itself by performing the following:
NOTE: Newer versions of Ubuntu do not need the line ‘sudo apt update’ since the update command is performed automatically after a repository is added.
The ‘modprobe’ command is used to place modules in the kernel so they are loaded automatically when Linux starts.
Generate Public/Private Keys
The Public/Private Keys are important since they are used for the encryption of packets between the Wireguard systems. First, you need to make a folder in which to create the keys and then create the keys as follows:
Whenever you generate a new Private Key you must also generate a Public Key.
Adding Wireguard Interface
A virtual interface must be made to allow for communication between the Wireguard clients. The name should be kept simple and you use the interface name for configuring each interface.
For this example we will use the interface name of ‘wg0’. If multiple interfaces must be created you can simply use ‘wg1’, ‘wg2’ and so on.
Set Up VPN Peers
Since we have a virtual interface it can now be configured. Assume there are only two clients to be connected together and the following information will be used:
Name: Host 1
Public IP: 10.1.0.207/8
Virtual IP: 192.168.0.1/24
Port: 7777
Public Key: wHUwN6I3wGaOXRw5rjxIMPZrjRRSMWEYok6PtytfJGU=
Name: Host 2
Public IP: 10.2.0.13/8
Virtual IP: 192.168.0.2/24
Port: 8888
Public Key: CbX0FSQ7W2LNMnozcMeTUrru6me+Q0tbbIfNlcBzPzs=
For HOST 1 the following commands would be executed in a Terminal:
For Host 2 the following would be executed in a Terminal:
The first line assigns an IP address to the interface. Line two specifies the Port used to listen on for incoming connections. On the third line is the location of the private key to use for the connection.
NOTE: Be aware that Port 65535 is the limit to the highest port number you can specify since there are only 65535 TCP/UDP Ports available. After 65535 the numbers start over at zero. Port 65536 is not allowed since it starts over at zero and 65537 is Port 1.
The last line specifies the Public Key for the other system as well as its virtual and public IP address with its Port. The Public Key must be sent from the other system (not the Private Key).
Other systems can be added, but the setup needs to be executed on each system that needs to communicate with one another. You can create multiple virtual interfaces by specifying a different name other than ‘wg0’.
Be aware that you may have to open the specific Ports in a Firewall to allow the VPN to go through a Firewall.
Enable the Wireguard Interface
Once the virtual interface has been created you only need to enable it to start the VPN. The interface needs to be enabled on all systems that are creating a VPN. The command to enable the interface is:
After the virtual interface has been created you can run ‘ifconfig’ to determine that the interface is enabled.
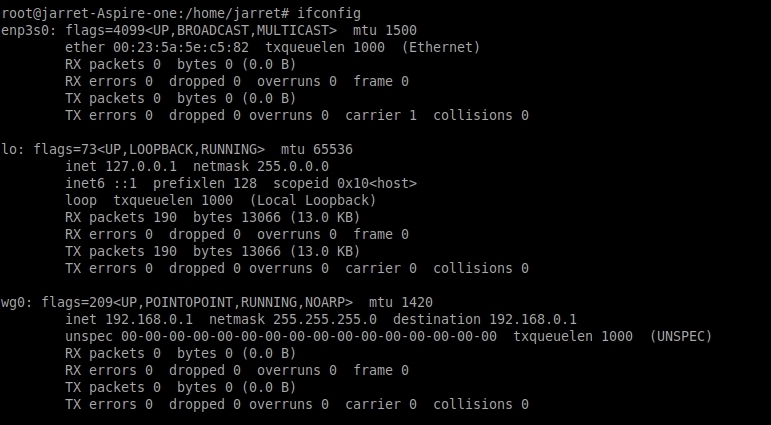
FIGURE 1
NOTE: You can also use the command ‘ip addr show’ to see interface information.
Testing the VPN Connection
Once the VPN has been established it is easy to determine that the connection has been made. Simply PING the address of the virtual interface.
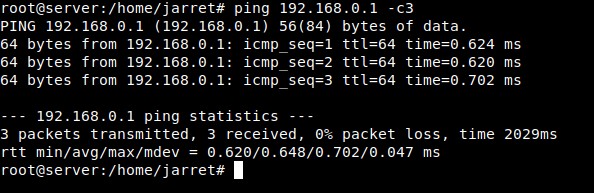
FIGURE 2
Removing Wireguard Interface
If you need to disable the virtual interface you can run the command:
All of the settings for the virtual interface are intact and you only need to enable the interface again.
To completely delete the interface run the command:
Recovering the VPN Connection
Once the system is rebooted all of the settings are lost. All of the commands entered to create the VPN can be placed into a BASH script and executed at once.
Another option is to save the settings to be easily reloaded later. Once all of the settings are made and the interface is enabled you can run the following command to save the settings:
If you want to use a different name for the configuration file you can, but remember the name.
After it is saved you can open the newly created file using a text editor. The first line is ‘[Interface]’ and you need to add a blank line for the second line. In this new blank line you should enter ‘Address = ‘ and type in your virtual IP address for the local system. Save the file and close the editor.
Anytime your restart the system and need to create the Wireguard interface you run the following command:
If you used a name other than ‘wg0’ for the saved configuration you just replace it in the command. The interface name will be what you call the configuration file. For example, if you name the configuration file ‘test’ then the Wireguard interface will be called ‘test’.
Hopefully you can get a VPN going between two systems by using this article. If you have a need for a VPN then try this out. Wireguard is a very simple program to use once you get used to setting it up.
Installing Wireguard is a straightforward procedure. Start by installing the Linux header files for your kernel using the following command :
Code:
sudo apt install linux-headers-$(uname -r)The results of ‘$(uname -r)’ fill in the current kernel version. Make sure the current running kernel is the version you want to be using for Wireguard.
Now you can install Wireguard itself by performing the following:
Code:
sudo add-apt-repository ppa:wireguard/wireguard
sudo apt update
sudo apt install wireguard
sudo modprobe wireguardNOTE: Newer versions of Ubuntu do not need the line ‘sudo apt update’ since the update command is performed automatically after a repository is added.
The ‘modprobe’ command is used to place modules in the kernel so they are loaded automatically when Linux starts.
Generate Public/Private Keys
The Public/Private Keys are important since they are used for the encryption of packets between the Wireguard systems. First, you need to make a folder in which to create the keys and then create the keys as follows:
Code:
sudo su
cd /etc/wireguard
umask 077
wg genkey > privatekey
wg pubkey < privatekey > publickeyWhenever you generate a new Private Key you must also generate a Public Key.
Adding Wireguard Interface
A virtual interface must be made to allow for communication between the Wireguard clients. The name should be kept simple and you use the interface name for configuring each interface.
For this example we will use the interface name of ‘wg0’. If multiple interfaces must be created you can simply use ‘wg1’, ‘wg2’ and so on.
Code:
ip link add dev wg0 type wireguardSet Up VPN Peers
Since we have a virtual interface it can now be configured. Assume there are only two clients to be connected together and the following information will be used:
Name: Host 1
Public IP: 10.1.0.207/8
Virtual IP: 192.168.0.1/24
Port: 7777
Public Key: wHUwN6I3wGaOXRw5rjxIMPZrjRRSMWEYok6PtytfJGU=
Name: Host 2
Public IP: 10.2.0.13/8
Virtual IP: 192.168.0.2/24
Port: 8888
Public Key: CbX0FSQ7W2LNMnozcMeTUrru6me+Q0tbbIfNlcBzPzs=
For HOST 1 the following commands would be executed in a Terminal:
Code:
sudo su
ip address add dev wg0 192.168.0.1/24
wg set wg0 listen-port 7777
wg set wg0 private-key /etc/wireguard/privatekey
wg set wg0 peer CbX0FSQ7W2LNMnozcMeTUrru6me+Q0tbbIfNlcBzPzs= allowed-ips 192.168.0.2/24 endpoint 10.2.0.13:8888For Host 2 the following would be executed in a Terminal:
Code:
sudo su
ip address add dev wg0 192.168.0.2/24
wg set wg0 listen-port 8888
wg set wg0 private-key /etc/wireguard/privatekey
wg set wg0 peer wHUwN6I3wGaOXRw5rjxIMPZrjRRSMWEYok6PtytfJGU= allowed-ips 192.168.0.1/24 endpoint 10.1.0.207:7777The first line assigns an IP address to the interface. Line two specifies the Port used to listen on for incoming connections. On the third line is the location of the private key to use for the connection.
NOTE: Be aware that Port 65535 is the limit to the highest port number you can specify since there are only 65535 TCP/UDP Ports available. After 65535 the numbers start over at zero. Port 65536 is not allowed since it starts over at zero and 65537 is Port 1.
The last line specifies the Public Key for the other system as well as its virtual and public IP address with its Port. The Public Key must be sent from the other system (not the Private Key).
Other systems can be added, but the setup needs to be executed on each system that needs to communicate with one another. You can create multiple virtual interfaces by specifying a different name other than ‘wg0’.
Be aware that you may have to open the specific Ports in a Firewall to allow the VPN to go through a Firewall.
Enable the Wireguard Interface
Once the virtual interface has been created you only need to enable it to start the VPN. The interface needs to be enabled on all systems that are creating a VPN. The command to enable the interface is:
Code:
ip link set up dev wg0After the virtual interface has been created you can run ‘ifconfig’ to determine that the interface is enabled.
FIGURE 1
NOTE: You can also use the command ‘ip addr show’ to see interface information.
Testing the VPN Connection
Once the VPN has been established it is easy to determine that the connection has been made. Simply PING the address of the virtual interface.
FIGURE 2
Removing Wireguard Interface
If you need to disable the virtual interface you can run the command:
Code:
ip link set down dev wg0All of the settings for the virtual interface are intact and you only need to enable the interface again.
To completely delete the interface run the command:
Code:
ip link delete wg0Recovering the VPN Connection
Once the system is rebooted all of the settings are lost. All of the commands entered to create the VPN can be placed into a BASH script and executed at once.
Another option is to save the settings to be easily reloaded later. Once all of the settings are made and the interface is enabled you can run the following command to save the settings:
Code:
wg showconf wg0 | tee /etc/wireguard/wg0.confIf you want to use a different name for the configuration file you can, but remember the name.
After it is saved you can open the newly created file using a text editor. The first line is ‘[Interface]’ and you need to add a blank line for the second line. In this new blank line you should enter ‘Address = ‘ and type in your virtual IP address for the local system. Save the file and close the editor.
Anytime your restart the system and need to create the Wireguard interface you run the following command:
Code:
wg-quick up wg0If you used a name other than ‘wg0’ for the saved configuration you just replace it in the command. The interface name will be what you call the configuration file. For example, if you name the configuration file ‘test’ then the Wireguard interface will be called ‘test’.
Hopefully you can get a VPN going between two systems by using this article. If you have a need for a VPN then try this out. Wireguard is a very simple program to use once you get used to setting it up.
Last edited by a moderator:

