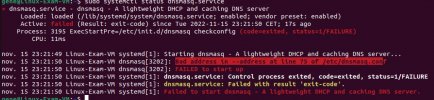
That's not actually what I asked for information. It might be helpful, because now it's showing an error on another line, specifically line 7. However, I'm a one problem at a time kinda guy.
Without knowing what those lines contain, I'm not sure that anyone can help you.
Hi i enter the command you gave me
Sorry about that and thanks for helping i appreciate that
cat -n /etc/dnsmasq.conf
1 # Configuration file for dnsmasq.
2 #
3 # Format is one option per line, legal options are the same
4 # as the long options legal on the command line. See
5 # "/usr/sbin/dnsmasq --help" or "man 8 dnsmasq" for details.
6
7 # Listen on this specific port instead of the standard DNS port
8 # (53). Setting this to zero completely disables DNS function,
9 # leaving only DHCP and/or TFTP.
10 port=53
11
12 # The following two options make you a better netizen, since they
13 # tell dnsmasq to filter out queries which the public DNS cannot
14 # answer, and which load the servers (especially the root servers)
15 # unnecessarily. If you have a dial-on-demand link they also stop
16 # these requests from bringing up the link unnecessarily.
17
18 # Never forward plain names (without a dot or domain part)
19 domain-needed
20 # Never forward addresses in the non-routed address spaces.
21 bogus-priv
22
23 # Uncomment these to enable DNSSEC validation and caching:
24 # (Requires dnsmasq to be built with DNSSEC option.)
25 #conf-file=%%PREFIX%%/share/dnsmasq/trust-anchors.conf
26 #dnssec
27
28 # Replies which are not DNSSEC signed may be legitimate, because the domain
29 # is unsigned, or may be forgeries. Setting this option tells dnsmasq to
30 # check that an unsigned reply is OK, by finding a secure proof that a DS
31 # record somewhere between the root and the domain does not exist.
32 # The cost of setting this is that even queries in unsigned domains will need
33 # one or more extra DNS queries to verify.
34 #dnssec-check-unsigned
35
36 # Uncomment this to filter useless windows-originated DNS requests
37 # which can trigger dial-on-demand links needlessly.
38 # Note that (amongst other things) this blocks all SRV requests,
39 # so don't use it if you use eg Kerberos, SIP, XMMP or Google-talk.
40 # This option only affects forwarding, SRV records originating for
41 # dnsmasq (via srv-host= lines) are not suppressed by it.
42 #filterwin2k
43
44 # Change this line if you want dns to get its upstream servers from
45 # somewhere other that /etc/resolv.conf
46 #resolv-file=
47
48 # By default, dnsmasq will send queries to any of the upstream
49 # servers it knows about and tries to favour servers to are known
50 # to be up. Uncommenting this forces dnsmasq to try each query
51 # with each server strictly in the order they appear in
52 # /etc/resolv.conf
53 strict-order
54
55 # If you don't want dnsmasq to read /etc/resolv.conf or any other
56 # file, getting its servers from this file instead (see below), then
57 # uncomment this.
58 #no-resolv
59
60 # If you don't want dnsmasq to poll /etc/resolv.conf or other resolv
61 # files for changes and re-read them then uncomment this.
62 #no-poll
63
64 # Add other name servers here, with domain specs if they are for
65 # non-public domains.
66 #server=/localnet/192.168.0.1
67
68 # Example of routing PTR queries to nameservers: this will send all
69 # address->name queries for 192.168.3/24 to nameserver 10.1.2.3
70 #server=/3.168.192.in-addr.arpa/10.1.2.3
71
72 # Add local-only domains here, queries in these domains are answered
73 # from /etc/hosts or DHCP only.
74 #local=/localnet/
75
76 # Add domains which you want to force to an IP address here.
77 # The example below send any host in double-click.net to a local
78 # web-server.
79 #address=/double-click.net/127.0.0.1
80
81 # --address (and --server) work with IPv6 addresses too.
82 #address=/www.thekelleys.org.uk/fe80::20d:60ff:fe36:f83
83
84 # Add the IPs of all queries to yahoo.com, google.com, and their
85 # subdomains to the vpn and search ipsets:
86 #ipset=/yahoo.com/google.com/vpn,search
87
88 # You can control how dnsmasq talks to a server: this forces
89 # queries to 10.1.2.3 to be routed via eth1
90 # server=10.1.2.3@eth1
91
92 # and this sets the source (ie local) address used to talk to
93 # 10.1.2.3 to 192.168.1.1 port 55 (there must be an interface with that
94 # IP on the machine, obviously).
95 # server=
[email protected]#55
96
97 # If you want dnsmasq to change uid and gid to something other
98 # than the default, edit the following lines.
99 #user=
100 #group=
101
102 # If you want dnsmasq to listen for DHCP and DNS requests only on
103 # specified interfaces (and the loopback) give the name of the
104 # interface (eg eth0) here.
105 # Repeat the line for more than one interface.
106 #interface=
107 # Or you can specify which interface _not_ to listen on
108 #except-interface=
109 # Or which to listen on by address (remember to include 127.0.0.1 if
110 # you use this.)
111 #listen-address=
112 # If you want dnsmasq to provide only DNS service on an interface,
113 # configure it as shown above, and then use the following line to
114 # disable DHCP and TFTP on it.
115 #no-dhcp-interface=
116
117 # On systems which support it, dnsmasq binds the wildcard address,
118 # even when it is listening on only some interfaces. It then discards
119 # requests that it shouldn't reply to. This has the advantage of
120 # working even when interfaces come and go and change address. If you
121 # want dnsmasq to really bind only the interfaces it is listening on,
122 # uncomment this option. About the only time you may need this is when
123 # running another nameserver on the same machine.
124 #bind-interfaces
125
126 # If you don't want dnsmasq to read /etc/hosts, uncomment the
127 # following line.
128 #no-hosts
129 # or if you want it to read another file, as well as /etc/hosts, use
130 # this.
131 #addn-hosts=/etc/banner_add_hosts
132
133 # Set this (and domain: see below) if you want to have a domain
134 # automatically added to simple names in a hosts-file.
135 expand-hosts
136
137 # Set the domain for dnsmasq. this is optional, but if it is set, it
138 # does the following things.
139 # 1) Allows DHCP hosts to have fully qualified domain names, as long
140 # as the domain part matches this setting.
141 # 2) Sets the "domain" DHCP option thereby potentially setting the
142 # domain of all systems configured by DHCP
143 # 3) Provides the domain part for "expand-hosts"
144 #domain=thekelleys.org.uk
145 domain=example.com
146 # Set a different domain for a particular subnet
147 #domain=wireless.thekelleys.org.uk,192.168.2.0/24
148
149 # Set Listen address
150 listen-address=127.0.0.1 # Set to Server IP for network responses
151
152 # Same idea, but range rather then subnet
153 #domain=reserved.thekelleys.org.uk,192.68.3.100,192.168.3.200
154
155 # Uncomment this to enable the integrated DHCP server, you need
156 # to supply the range of addresses available for lease and optionally
157 # a lease time. If you have more than one network, you will need to
158 # repeat this for each network on which you want to supply DHCP
159 # service.
160 #dhcp-range=192.168.0.50,192.168.0.150,12h
161
162 # This is an example of a DHCP range where the netmask is given. This
163 # is needed for networks we reach the dnsmasq DHCP server via a relay
164 # agent. If you don't know what a DHCP relay agent is, you probably
165 # don't need to worry about this.
166 #dhcp-range=192.168.0.50,192.168.0.150,255.255.255.0,12h
167
168 # This is an example of a DHCP range which sets a tag, so that
169 # some DHCP options may be set only for this network.
170 #dhcp-range=set:red,192.168.0.50,192.168.0.150
171
172 # Use this DHCP range only when the tag "green" is set.
173 #dhcp-range=tag:green,192.168.0.50,192.168.0.150,12h
174
175 # Specify a subnet which can't be used for dynamic address allocation,
176 # is available for hosts with matching --dhcp-host lines. Note that
177 # dhcp-host declarations will be ignored unless there is a dhcp-range
178 # of some type for the subnet in question.
179 # In this case the netmask is implied (it comes from the network
180 # configuration on the machine running dnsmasq) it is possible to give
181 # an explicit netmask instead.
182 #dhcp-range=192.168.0.0,static
183
184 # Enable DHCPv6. Note that the prefix-length does not need to be specified
185 # and defaults to 64 if missing/
186 #dhcp-range=1234::2, 1234::500, 64, 12h
187
188 # Do Router Advertisements, BUT NOT DHCP for this subnet.
189 #dhcp-range=1234::, ra-only
190
191 # Do Router Advertisements, BUT NOT DHCP for this subnet, also try and
192 # add names to the DNS for the IPv6 address of SLAAC-configured dual-stack
193 # hosts. Use the DHCPv4 lease to derive the name, network segment and
194 # MAC address and assume that the host will also have an
195 # IPv6 address calculated using the SLAAC algorithm.
196 #dhcp-range=1234::, ra-names
197
198 # Do Router Advertisements, BUT NOT DHCP for this subnet.
199 # Set the lifetime to 46 hours. (Note: minimum lifetime is 2 hours.)
200 #dhcp-range=1234::, ra-only, 48h
201
202 # Do DHCP and Router Advertisements for this subnet. Set the A bit in the RA
203 # so that clients can use SLAAC addresses as well as DHCP ones.
204 #dhcp-range=1234::2, 1234::500, slaac
205
206 # Do Router Advertisements and stateless DHCP for this subnet. Clients will
207 # not get addresses from DHCP, but they will get other configuration information.
208 # They will use SLAAC for addresses.
209 #dhcp-range=1234::, ra-stateless
210
211 # Do stateless DHCP, SLAAC, and generate DNS names for SLAAC addresses
212 # from DHCPv4 leases.
213 #dhcp-range=1234::, ra-stateless, ra-names
214
215 # Do router advertisements for all subnets where we're doing DHCPv6
216 # Unless overridden by ra-stateless, ra-names, et al, the router
217 # advertisements will have the M and O bits set, so that the clients
218 # get addresses and configuration from DHCPv6, and the A bit reset, so the
219 # clients don't use SLAAC addresses.
220 #enable-ra
221
222 # Supply parameters for specified hosts using DHCP. There are lots
223 # of valid alternatives, so we will give examples of each. Note that
224 # IP addresses DO NOT have to be in the range given above, they just
225 # need to be on the same network. The order of the parameters in these
226 # do not matter, it's permissible to give name, address and MAC in any
227 # order.
228
229 # Always allocate the host with Ethernet address 11:22:33:44:55:66
230 # The IP address 192.168.0.60
231 #dhcp-host=11:22:33:44:55:66,192.168.0.60
232
233 # Always set the name of the host with hardware address
234 # 11:22:33:44:55:66 to be "fred"
235 #dhcp-host=11:22:33:44:55:66,fred
236
237 # Always give the host with Ethernet address 11:22:33:44:55:66
238 # the name fred and IP address 192.168.0.60 and lease time 45 minutes
239 #dhcp-host=11:22:33:44:55:66,fred,192.168.0.60,45m
240
241 # Give a host with Ethernet address 11:22:33:44:55:66 or
242 # 12:34:56:78:90:12 the IP address 192.168.0.60. Dnsmasq will assume
243 # that these two Ethernet interfaces will never be in use at the same
244 # time, and give the IP address to the second, even if it is already
245 # in use by the first. Useful for laptops with wired and wireless
246 # addresses.
247 #dhcp-host=11:22:33:44:55:66,12:34:56:78:90:12,192.168.0.60
248
249 # Give the machine which says its name is "bert" IP address
250 # 192.168.0.70 and an infinite lease
251 #dhcp-host=bert,192.168.0.70,infinite
252
253 # Always give the host with client identifier 01:02:02:04
254 # the IP address 192.168.0.60
255 #dhcp-host=id:01:02:02:04,192.168.0.60
256
257 # Always give the InfiniBand interface with hardware address
258 # 80:00:00:48:fe:80:00:00:00:00:00:00:f4:52:14:03:00:28:05:81 the
259 # ip address 192.168.0.61. The client id is derived from the prefix
260 # ff:00:00:00:00:00:02:00:00:02:c9:00 and the last 8 pairs of
261 # hex digits of the hardware address.
262 #dhcp-host=id:ff:00:00:00:00:00:02:00:00:02:c9:00:f4:52:14:03:00:28:05:81,192.168.0.61
263
264 # Always give the host with client identifier "marjorie"
265 # the IP address 192.168.0.60
266 #dhcp-host=id:marjorie,192.168.0.60
267
268 # Enable the address given for "judge" in /etc/hosts
269 # to be given to a machine presenting the name "judge" when
270 # it asks for a DHCP lease.
271 #dhcp-host=judge
272
273 # Never offer DHCP service to a machine whose Ethernet
274 # address is 11:22:33:44:55:66
275 #dhcp-host=11:22:33:44:55:66,ignore
276
277 # Ignore any client-id presented by the machine with Ethernet
278 # address 11:22:33:44:55:66. This is useful to prevent a machine
279 # being treated differently when running under different OS's or
280 # between PXE boot and OS boot.
281 #dhcp-host=11:22:33:44:55:66,id:*
282
283 # Send extra options which are tagged as "red" to
284 # the machine with Ethernet address 11:22:33:44:55:66
285 #dhcp-host=11:22:33:44:55:66,set:red
286
287 # Send extra options which are tagged as "red" to
288 # any machine with Ethernet address starting 11:22:33:
289 #dhcp-host=11:22:33:*:*:*,set:red
290
291 # Give a fixed IPv6 address and name to client with
292 # DUID 00:01:00:01:16:d2:83:fc:92:d4:19:e2:d8:b2
293 # Note the MAC addresses CANNOT be used to identify DHCPv6 clients.
294 # Note also that the [] around the IPv6 address are obligatory.
295 #dhcp-host=id:00:01:00:01:16:d2:83:fc:92:d4:19:e2:d8:b2, fred, [1234::5]
296
297 # Ignore any clients which are not specified in dhcp-host lines
298 # or /etc/ethers. Equivalent to ISC "deny unknown-clients".
299 # This relies on the special "known" tag which is set when
300 # a host is matched.
301 #dhcp-ignore=tag:!known
302
303 # Send extra options which are tagged as "red" to any machine whose
304 # DHCP vendorclass string includes the substring "Linux"
305 #dhcp-vendorclass=set:red,Linux
306
307 # Send extra options which are tagged as "red" to any machine one
308 # of whose DHCP userclass strings includes the substring "accounts"
309 #dhcp-userclass=set:red,accounts
310
311 # Send extra options which are tagged as "red" to any machine whose
312 # MAC address matches the pattern.
313 #dhcp-mac=set:red,00:60:8C:*:*:*
314
315 # If this line is uncommented, dnsmasq will read /etc/ethers and act
316 # on the ethernet-address/IP pairs found there just as if they had
317 # been given as --dhcp-host options. Useful if you keep
318 # MAC-address/host mappings there for other purposes.
319 #read-ethers
320
321 # Send options to hosts which ask for a DHCP lease.
322 # See RFC 2132 for details of available options.
323 # Common options can be given to dnsmasq by name:
324 # run "dnsmasq --help dhcp" to get a list.
325 # Note that all the common settings, such as netmask and
326 # broadcast address, DNS server and default route, are given
327 # sane defaults by dnsmasq. You very likely will not need
328 # any dhcp-options. If you use Windows clients and Samba, there
329 # are some options which are recommended, they are detailed at the
330 # end of this section.
331
332 # Override the default route supplied by dnsmasq, which assumes the
333 # router is the same machine as the one running dnsmasq.
334 #dhcp-option=3,1.2.3.4
335
336 # Do the same thing, but using the option name
337 #dhcp-option=option:router,1.2.3.4
338
339 # Override the default route supplied by dnsmasq and send no default
340 # route at all. Note that this only works for the options sent by
341 # default (1, 3, 6, 12, 28) the same line will send a zero-length option
342 # for all other option numbers.
343 #dhcp-option=3
344
345 # Set the NTP time server addresses to 192.168.0.4 and 10.10.0.5
346 #dhcp-option=option:ntp-server,192.168.0.4,10.10.0.5
347
348 # Send DHCPv6 option. Note [] around IPv6 addresses.
349 #dhcp-option=option6:dns-server,[1234::77],[1234::88]
350
351 # Send DHCPv6 option for namservers as the machine running
352 # dnsmasq and another.
353 #dhcp-option=option6:dns-server,[::],[1234::88]
354
355 # Ask client to poll for option changes every six hours. (RFC4242)
356 #dhcp-option=option6:information-refresh-time,6h
357
358 # Set option 58 client renewal time (T1). Defaults to half of the
359 # lease time if not specified. (RFC2132)
360 #dhcp-option=option:T1,1m
361
362 # Set option 59 rebinding time (T2). Defaults to 7/8 of the
363 # lease time if not specified. (RFC2132)
364 #dhcp-option=option:T2,2m
365
366 # Set the NTP time server address to be the same machine as
367 # is running dnsmasq
368 #dhcp-option=42,0.0.0.0
369
370 # Set the NIS domain name to "welly"
371 #dhcp-option=40,welly
372
373 # Set the default time-to-live to 50
374 #dhcp-option=23,50
375
376 # Set the "all subnets are local" flag
377 #dhcp-option=27,1
378
379 # Send the etherboot magic flag and then etherboot options (a string).
380 #dhcp-option=128,e4:45:74:68:00:00
381 #dhcp-option=129,NIC=eepro100
382
383 # Specify an option which will only be sent to the "red" network
384 # (see dhcp-range for the declaration of the "red" network)
385 # Note that the tag: part must precede the option: part.
386 #dhcp-option = tag:red, option:ntp-server, 192.168.1.1
387
388 # The following DHCP options set up dnsmasq in the same way as is specified
389 # for the ISC dhcpcd in
390 #
http://www.samba.org/samba/ftp/docs/textdocs/DHCP-Server-Configuration.txt
391 # adapted for a typical dnsmasq installation where the host running
392 # dnsmasq is also the host running samba.
393 # you may want to uncomment some or all of them if you use
394 # Windows clients and Samba.
395 #dhcp-option=19,0 # option ip-forwarding off
396 #dhcp-option=44,0.0.0.0 # set netbios-over-TCP/IP nameserver(s) aka WINS server(s)
397 #dhcp-option=45,0.0.0.0 # netbios datagram distribution server
398 #dhcp-option=46,8 # netbios node type
399
400 # Send an empty WPAD option. This may be REQUIRED to get windows 7 to behave.
401 #dhcp-option=252,"\n"
402
403 # Send RFC-3397 DNS domain search DHCP option. WARNING: Your DHCP client
404 # probably doesn't support this......
405 #dhcp-option=option:domain-search,eng.apple.com,marketing.apple.com
406
407 # Send RFC-3442 classless static routes (note the netmask encoding)
408 #dhcp-option=121,192.168.1.0/24,1.2.3.4,10.0.0.0/8,5.6.7.8
409
410 # Send vendor-class specific options encapsulated in DHCP option 43.
411 # The meaning of the options is defined by the vendor-class so
412 # options are sent only when the client supplied vendor class
413 # matches the class given here. (A substring match is OK, so "MSFT"
414 # matches "MSFT" and "MSFT 5.0"). This example sets the
415 # mtftp address to 0.0.0.0 for PXEClients.
416 #dhcp-option=vendor

XEClient,1,0.0.0.0
417
418 # Send microsoft-specific option to tell windows to release the DHCP lease
419 # when it shuts down. Note the "i" flag, to tell dnsmasq to send the
420 # value as a four-byte integer - that's what microsoft wants. See
421 #
http://technet2.microsoft.com/Windo...d2d4-49f0-96d6-4b7414ecfaae1033.mspx?mfr=true
422 #dhcp-option=vendor:MSFT,2,1i
423
424 # Send the Encapsulated-vendor-class ID needed by some configurations of
425 # Etherboot to allow is to recognise the DHCP server.
426 #dhcp-option=vendor:Etherboot,60,"Etherboot"
427
428 # Send options to PXELinux. Note that we need to send the options even
429 # though they don't appear in the parameter request list, so we need
430 # to use dhcp-option-force here.
431 # See
http://syslinux.zytor.com/pxe.php#special for details.
432 # Magic number - needed before anything else is recognised
433 #dhcp-option-force=208,f1:00:74:7e
434 # Configuration file name
435 #dhcp-option-force=209,configs/common
436 # Path prefix
437 #dhcp-option-force=210,/tftpboot/pxelinux/files/
438 # Reboot time. (Note 'i' to send 32-bit value)
439 #dhcp-option-force=211,30i
440
441 # Set the boot filename for netboot/PXE. You will only need
442 # this if you want to boot machines over the network and you will need
443 # a TFTP server; either dnsmasq's built-in TFTP server or an
444 # external one. (See below for how to enable the TFTP server.)
445 #dhcp-boot=pxelinux.0
446
447 # The same as above, but use custom tftp-server instead machine running dnsmasq
448 #dhcp-boot=pxelinux,server.name,192.168.1.100
449
450 # Boot for iPXE. The idea is to send two different
451 # filenames, the first loads iPXE, and the second tells iPXE what to
452 # load. The dhcp-match sets the ipxe tag for requests from iPXE.
453 #dhcp-boot=undionly.kpxe
454 #dhcp-match=set:ipxe,175 # iPXE sends a 175 option.
455 #dhcp-boot=tag:ipxe,
http://boot.ipxe.org/demo/boot.php
456
457 # Encapsulated options for iPXE. All the options are
458 # encapsulated within option 175
459 #dhcp-option=encap:175, 1, 5b # priority code
460 #dhcp-option=encap:175, 176, 1b # no-proxydhcp
461 #dhcp-option=encap:175, 177, string # bus-id
462 #dhcp-option=encap:175, 189, 1b # BIOS drive code
463 #dhcp-option=encap:175, 190, user # iSCSI username
464 #dhcp-option=encap:175, 191, pass # iSCSI password
465
466 # Test for the architecture of a netboot client. PXE clients are
467 # supposed to send their architecture as option 93. (See RFC 4578)
468 #dhcp-match=peecees, option:client-arch, 0 #x86-32
469 #dhcp-match=itanics, option:client-arch, 2 #IA64
470 #dhcp-match=hammers, option:client-arch, 6 #x86-64
471 #dhcp-match=mactels, option:client-arch, 7 #EFI x86-64
472
473 # Do real PXE, rather than just booting a single file, this is an
474 # alternative to dhcp-boot.
475 #pxe-prompt="What system shall I netboot?"
476 # or with timeout before first available action is taken:
477 #pxe-prompt="Press F8 for menu.", 60
478
479 # Available boot services. for PXE.
480 #pxe-service=x86PC, "Boot from local disk"
481
482 # Loads <tftp-root>/pxelinux.0 from dnsmasq TFTP server.
483 #pxe-service=x86PC, "Install Linux", pxelinux
484
485 # Loads <tftp-root>/pxelinux.0 from TFTP server at 1.2.3.4.
486 # Beware this fails on old PXE ROMS.
487 #pxe-service=x86PC, "Install Linux", pxelinux, 1.2.3.4
488
489 # Use bootserver on network, found my multicast or broadcast.
490 #pxe-service=x86PC, "Install windows from RIS server", 1
491
492 # Use bootserver at a known IP address.
493 #pxe-service=x86PC, "Install windows from RIS server", 1, 1.2.3.4
494
495 # If you have multicast-FTP available,
496 # information for that can be passed in a similar way using options 1
497 # to 5. See page 19 of
498 #
http://download.intel.com/design/archives/wfm/downloads/pxespec.pdf
499